Ensuring the best possible preventative measures isn't always about getting more security tools. Most organizations already have a wide range of advanced tools in place. However, there's still a challenge in fully utilizing the capabilities of these existing tools. It's all about effectively using the capabilities you're licensed for to bridge the gap between assessing risks and managing them. The challenge lies not only in understanding and identifying what you're licensed for but also in deploying the optimal combination of these capabilities to mitigate and manage risk effectively.
We have written about how Reach will recommend specific controls within the tools you are using and how our integrations with Jira and ServiceNow will help create tickets to make the changes more efficient. But Reach also provides a way for you to automatically stage changes in a controlled environment.
In cybersecurity, it is important to maintain a stable and secure production environment by staging changes in a controlled manner. At Reach we understand the need for safety and control which is why our automation works in a staged environment before any changes go live.
Benefits of staged environment
The staged automation process at Reach offers many benefits, including:
Efficiency: Reach's automation significantly reduces the time and labor required for deploying changes. Processes that would typically be long and laborious are automated, freeing up valuable resources and allowing IT teams to focus on more strategic tasks. This not only enhances productivity but also accelerates the overall implementation timeline. Additionally, the streamlined collaboration process between security and IT departments is a key benefit. Security teams can define the necessary deployments and their risk mitigation impacts through detailed change tickets. IT can quickly approve these changes, ensuring efficient staging and deployment.
Increased Confidence: Knowing that changes have been tested and reviewed in a controlled environment instills confidence in the final deployment. Users can trust that the modifications will work as intended without causing unexpected issues.
Operational Continuity: By preventing disruptions in the production environment, organizations can maintain continuous operations and focus on their core business activities without worrying about system instability or downtime.
Reach automation with Conditional Access
Reach offers this staging automation across all the security tools we integrate with, one of these products is Conditional Access.
Here is an example of Reach’s automation with Conditional Access:
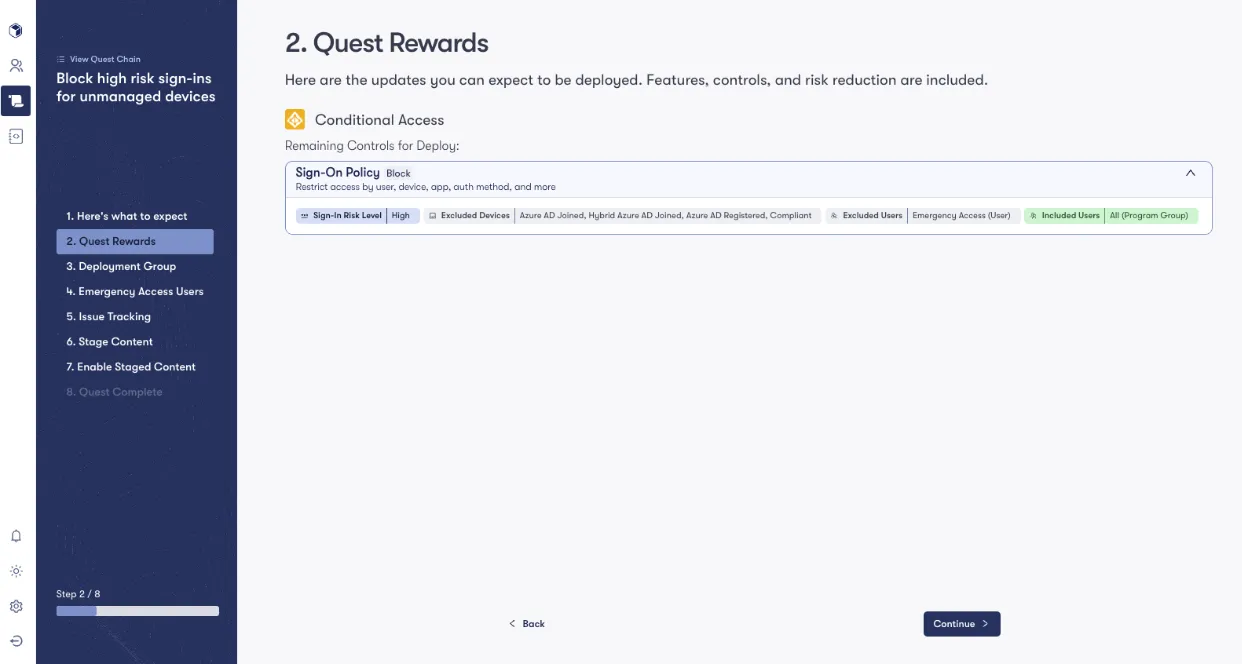
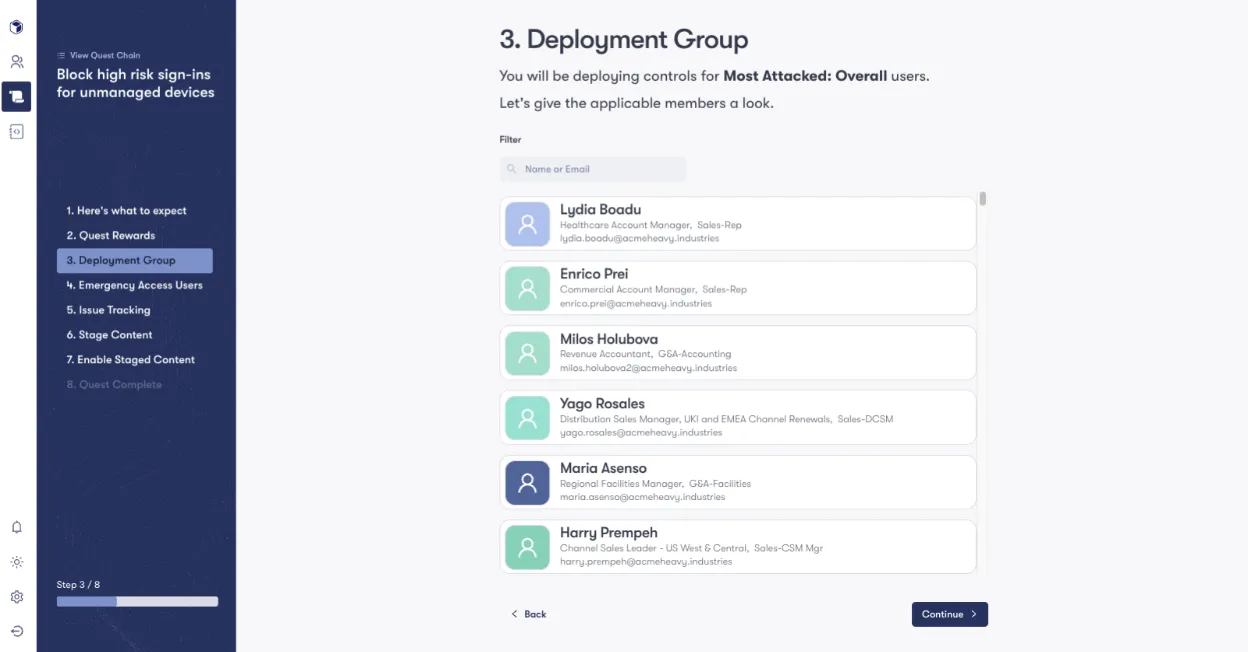
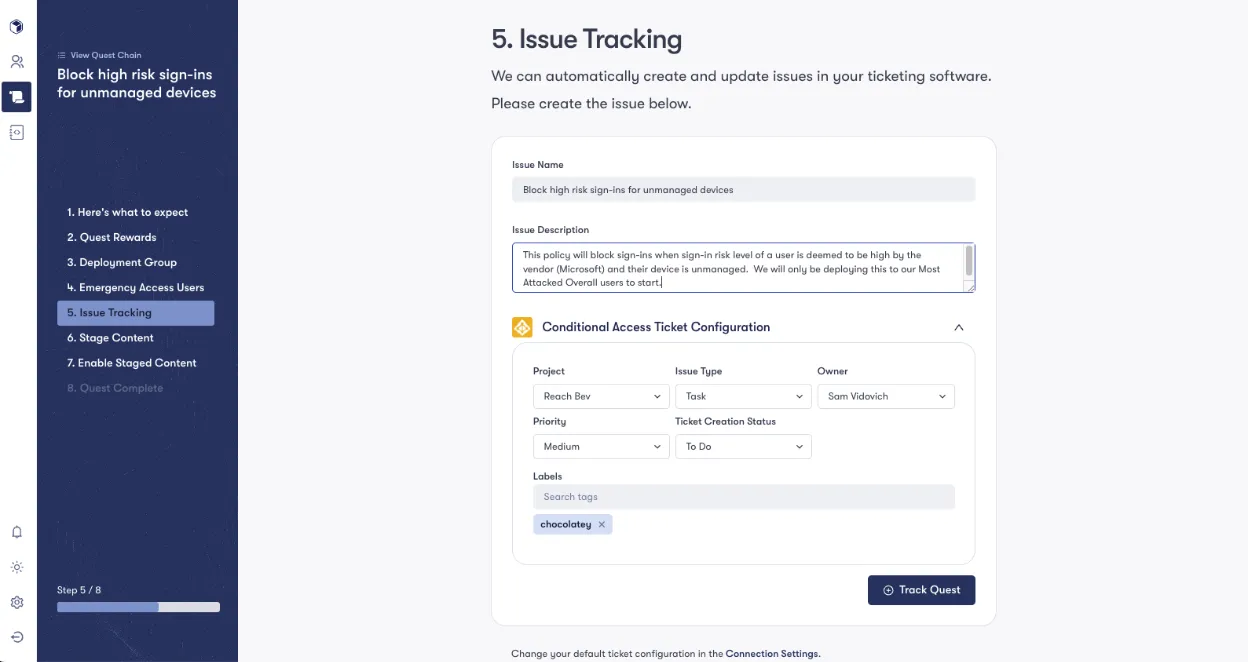
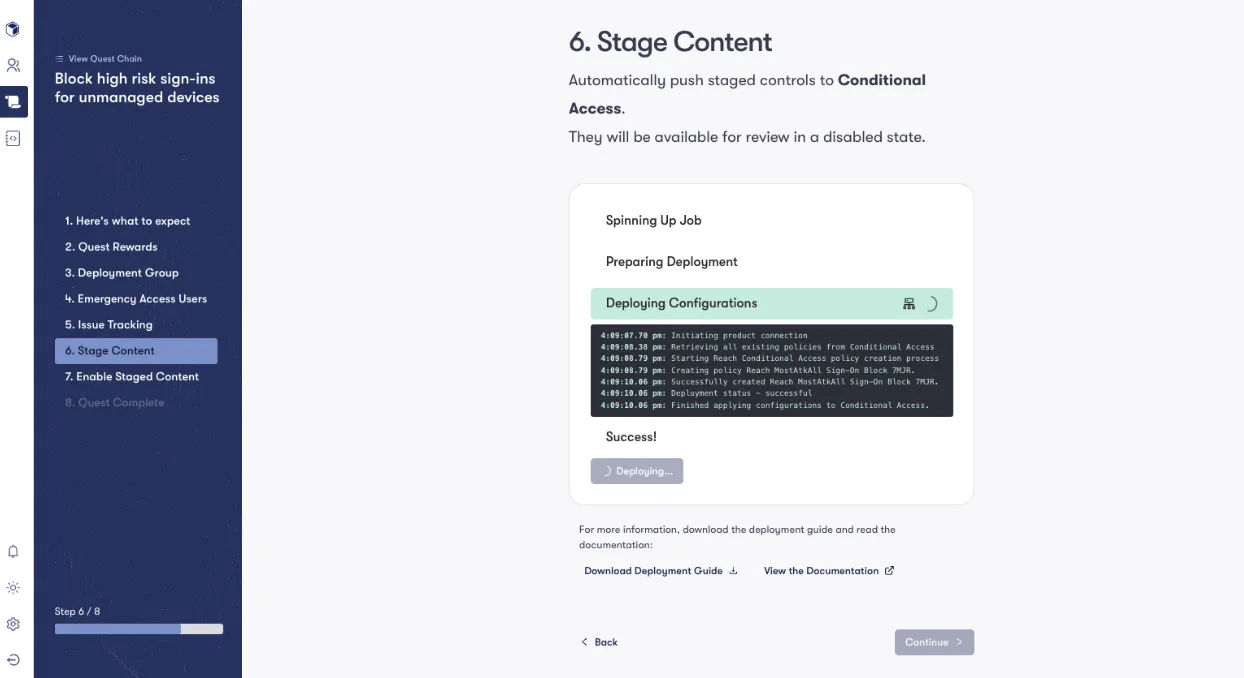
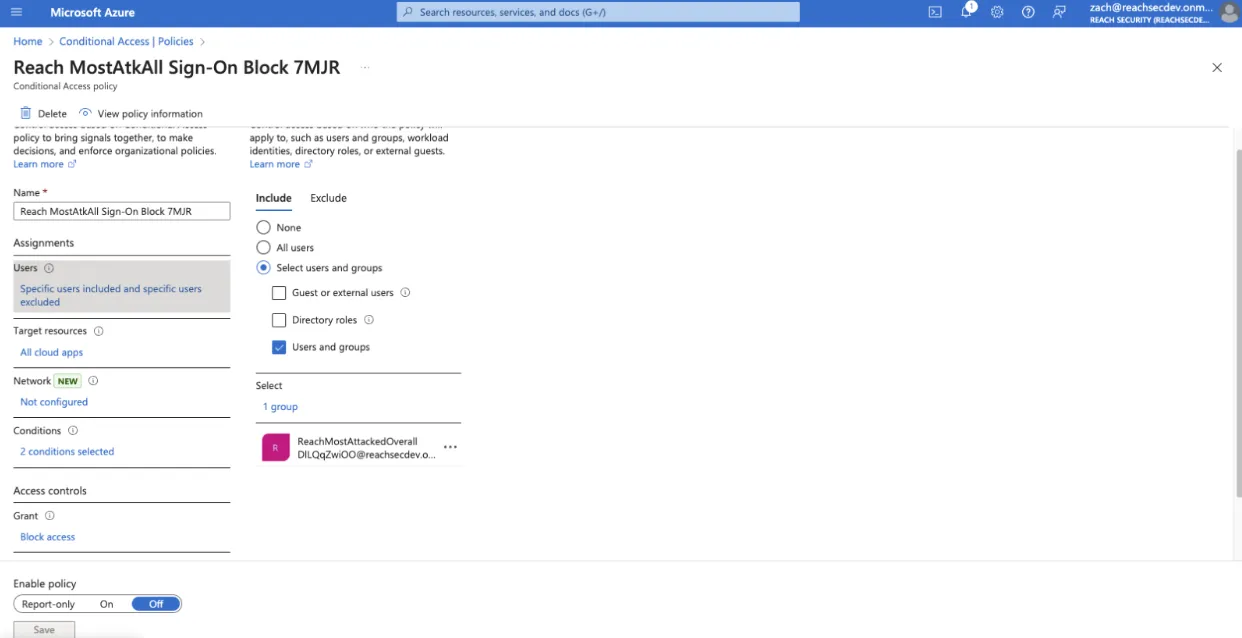
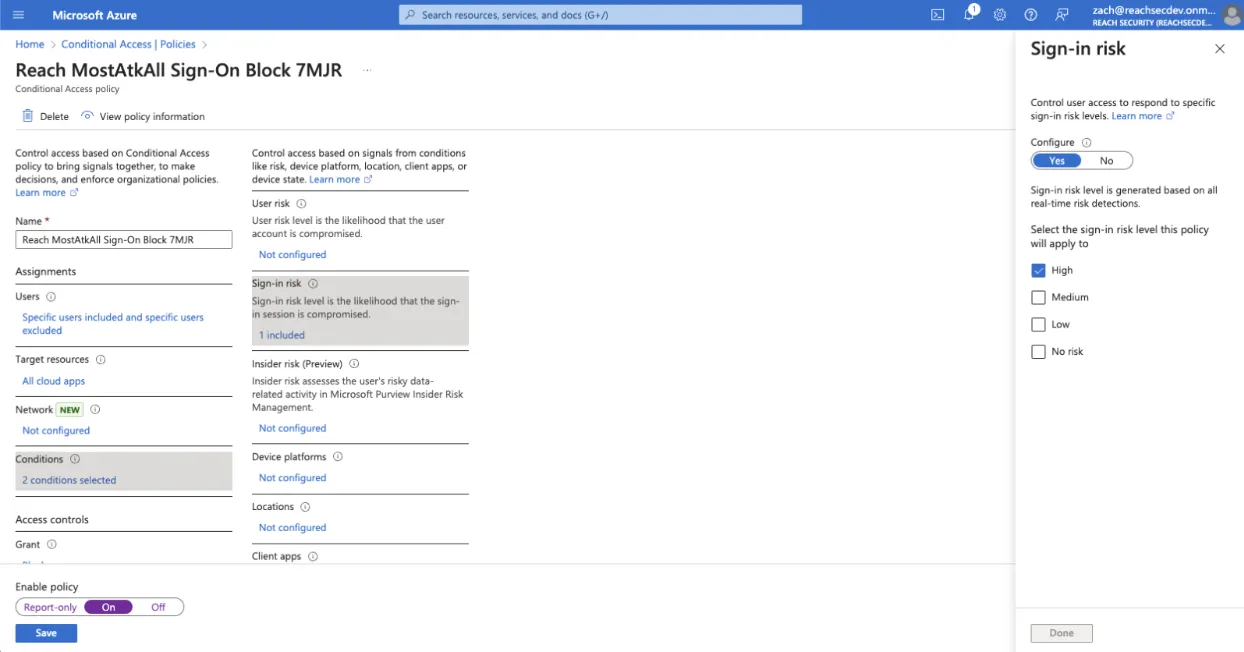
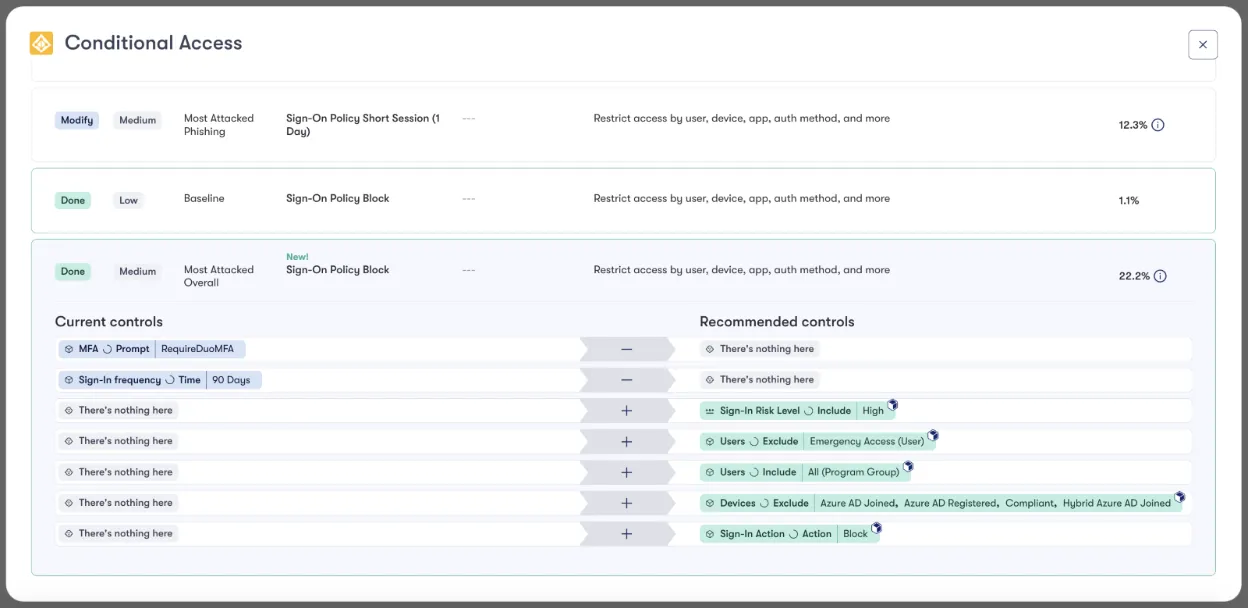
At Reach, we prioritize the safety and control of our users by leveraging a staged environment for automation. This approach not only safeguards the production environment but also ensures that changes are meticulously tested and approved before going live. Whether it’s implementing Conditional Access policies or deploying other critical updates, Reach’s staged automation empowers organizations to increase their cybersecurity posture with confidence, efficiency, and ease.
More About Reach Security
Reach is the first AI purpose-built to reprogram your security infrastructure based on who you are and how you're being attacked. Organizations of all sizes trust Reach to make mission-critical decisions because it doesn't hallucinate and it doesn't make mistakes. It's a different kind of AI. To learn more, visit reach.security/try-reach.










