New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download Now

Most breaches succeed because they exploit blind spots across your defense ecosystem.
Reach connects with your existing security infrastructure to automatically reveal hidden misconfigurations, underused security tool capabilities, and high risk users.

Reach prioritizes action based on the severity of exposure, attack behaviors, and configuration context - aligning control recommendations to your organization’s priorities. This lets you focus on fixes that reduce the most risk in the shortest amount of time.

Reach generates detailed step-by-step fixes, then executes tailored remediation workflows across your security ecosystem via integrations with your ticketing systems, aligned to MITRE, ZTNA, or your chosen framework. Reach doesn’t just surface issues – it fixes them for you automatically, at scale.
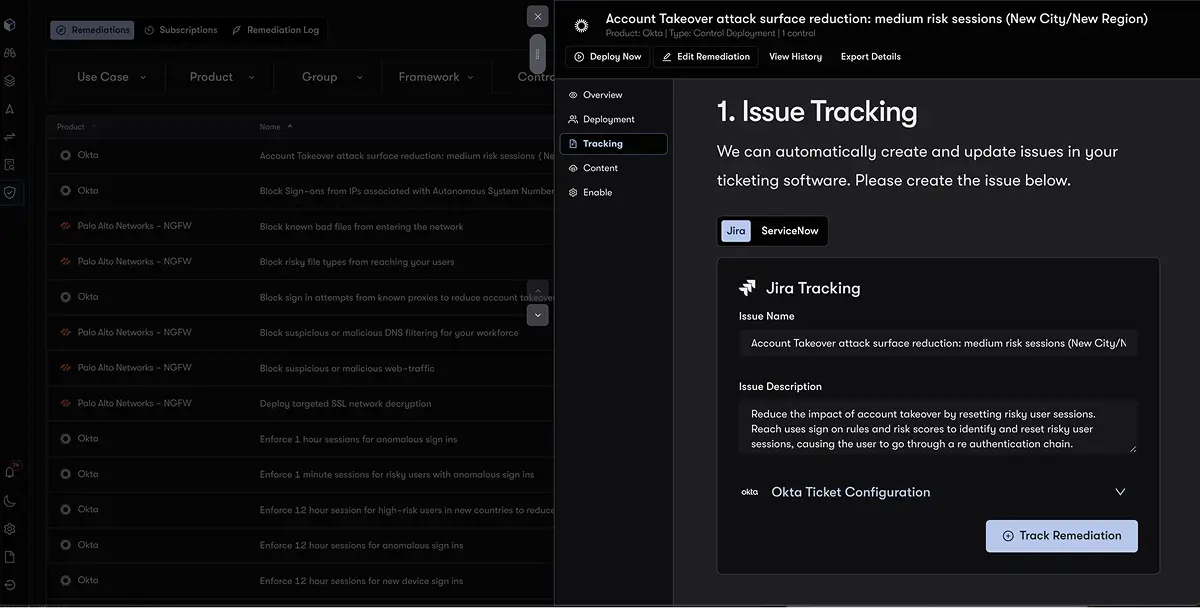
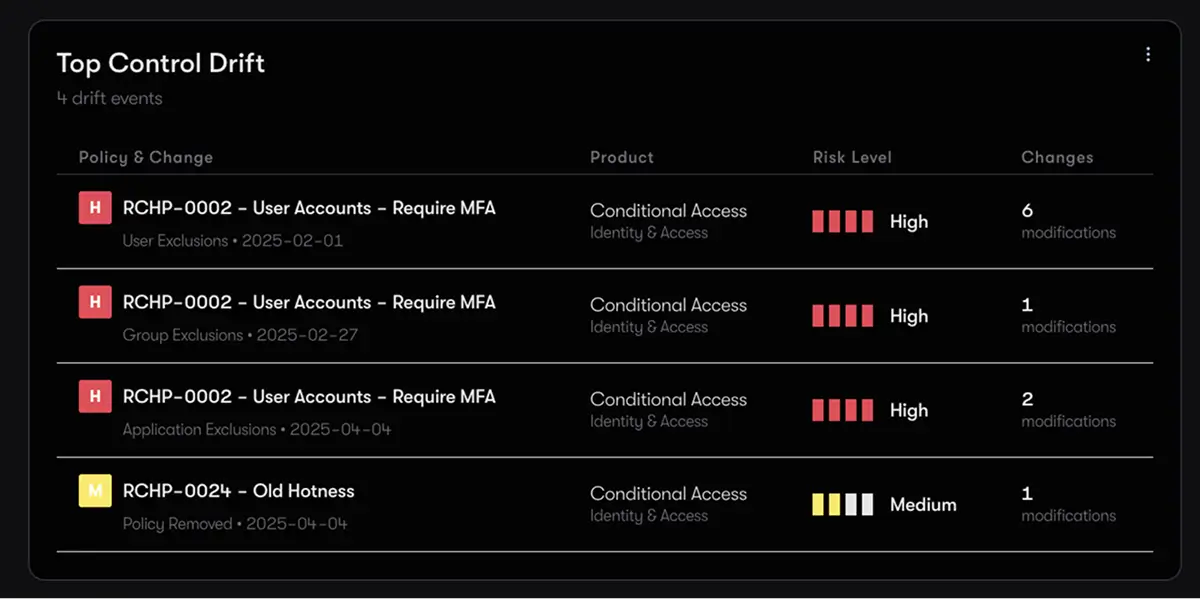
Security posture isn’t static. Reach continuously monitors your configurations over time to detect configuration drift the moment it happens, stop it, and validate that controls are working as intended. Achieve continuous visibility and control to stay ahead of change and ensure posture isn’t just assessed – it’s maintained.










Reach Integrations
Reach integrates seamlessly with your identity, endpoint protection, email security, and network security tool. With integrations into ticketing systems, Reach also helps you deploy configuration updates directly to your tools, turning insights into action and closing gaps quickly.
Success Stories
Discover how organizations like yours are exposing and eliminating hidden risk with Reach. These are their stories.
Unlock the full power of your security stack with a free tool rationalization assessment.
Read-only API key for a security tool of your choice
Create your account and setup the integration
Get results across licensing, control mapping, risk exposure, and posture