New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowModern security programs rely on a suite of tools - EDR, IAM, email security, firewalls - owned and operated by cross-functional teams. While this shared responsibility model brings flexibility, it also introduces operational risk: configurations change constantly, are left untouched in the event of break-glass situations, and changes are rarely communicated in real time.

Constantly changing configurations that are hard to track and easy to misalign

Unmonitored changes, including break-glass fixes, that quietly degrade security posture

Manual review and platform data often lag behind, exposing gaps only after the fact
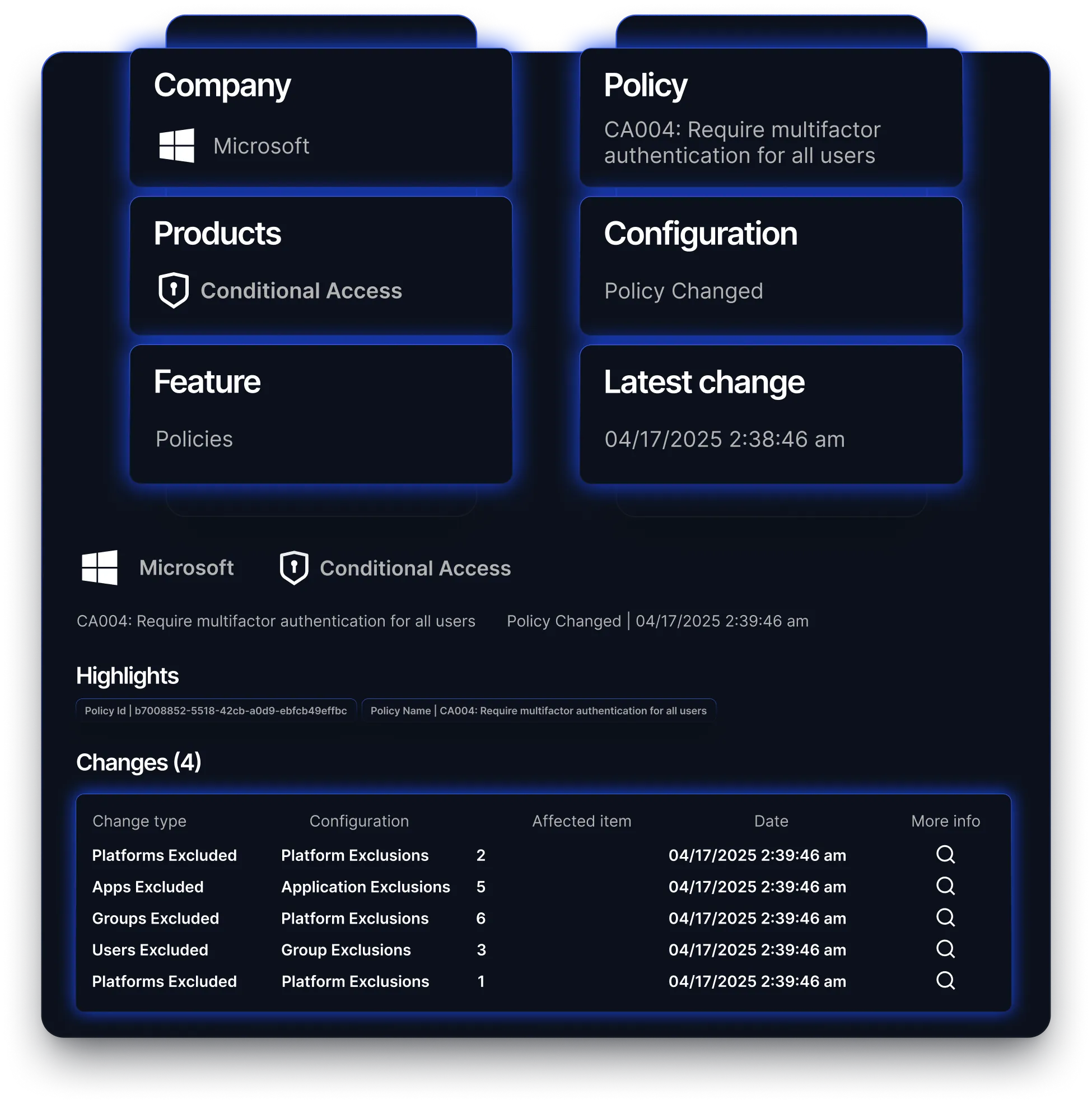
Track changes as they happen with real-time detection across product configurations, complete with metadata like feature, date, and source of change.
Security teams are overwhelmed by noise including endless logs, untracked updates, and no clear sense of what actually matters. Without filtering, drift alerts become just more noise, not insight.
Reach focuses on meaningful drift by highlighting only the configuration changes that impact security posture across IAM, EDR, firewalls, and more. This eliminates false positives and ensures teams focus their effort where it counts.
Posture doesn’t degrade all at once, it unravels silently through small, unmonitored changes. Manual reviews are slow, and by the time drift is discovered, it may already be a pathway for attack.
Reach gives you real-time visibility into impactful changes, with drift alerts tied to clear risk indicators. Teams can review, assign, and resolve issues directly from the platform before exposure spreads.
-min.webp)
Out-of-sync data between teams and tools leads to confusion, miscommunication, and missed risk. Customer conversations, audit prep, and operational planning suffer when no one has a current view.
Reach keeps your internal and external posture data aligned by logging changes, tracking status, and ensuring delivery teams always have the latest information. It’s a single source of truth for change you can act on.
-min.png)
Reach identifies and prioritizes exposure risks across email, network, endpoint, SaaS applications, and identity access management. By focusing on the most relevant threats, Reach helps organizations safeguard their most vulnerable asset: their people.
Reach automates remediation with context-driven recommendations, deployment guides, and change tickets tailored to your tools and environment. This ensures security changes are actionable, reducing the time and effort required to improve your security posture.
By connecting to existing tools, Reach provides a clear view of risk exposure, prioritizes based on your unique threat profile, and offers actionable insights. This approach empowers security teams to focus on what matters most, avoiding wasted efforts.
Unlike platforms that stop at assessments, Reach bridges the gap by guiding action. With deep integrations, automated prioritization, and tailored remediations, Reach enables organizations to reduce exposure and better utilize their existing tools.
To join the community of customers enjoying the benefits of Reach and learn more about how it can transform your security posture, visit:
-min.webp)