New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowIAM tools like MFA and SSO provide strong security, but many organizations struggle to configure them effectively. Without a risk-based approach, security capabilities remain underutilized, misaligned with threats, and difficult to enforce across teams.

Underutilized IAM Security Features

Misalignment Between Security and IT Teams

Lack of Granular, Risk-Based Policies

Reduction in attack anatomy risk
Total number of attacks

People in this group
1.2% of your organization
Reach analyzes your IAM environment to ensure you're fully leveraging security features like Conditional Access, adaptive MFA, and advanced sign-on policies.
Organizations struggle to understand and maximize the IAM security features they’re already paying for, leading to wasted potential and security gaps. Without clear insights, teams may not deploy advanced features like risk-based Conditional Access or adaptive MFA where they’re needed most.
Reach conducts a complete analysis of an organization’s IAM capabilities, distinguishing between basic and advanced features like P1 vs. P2 in Microsoft Entra ID or standard vs. adaptive MFA in Okta. This ensures security teams are fully utilizing their investments for maximum protection.

Total number of Attacks
Number of Attacks Delivered
Numbers of Attacks Preventable
IAM policies are often applied in broad strokes, failing to account for varying levels of user risk and attack patterns. Without fine-tuned controls, organizations either leave gaps or over-restrict access, frustrating users and increasing friction.
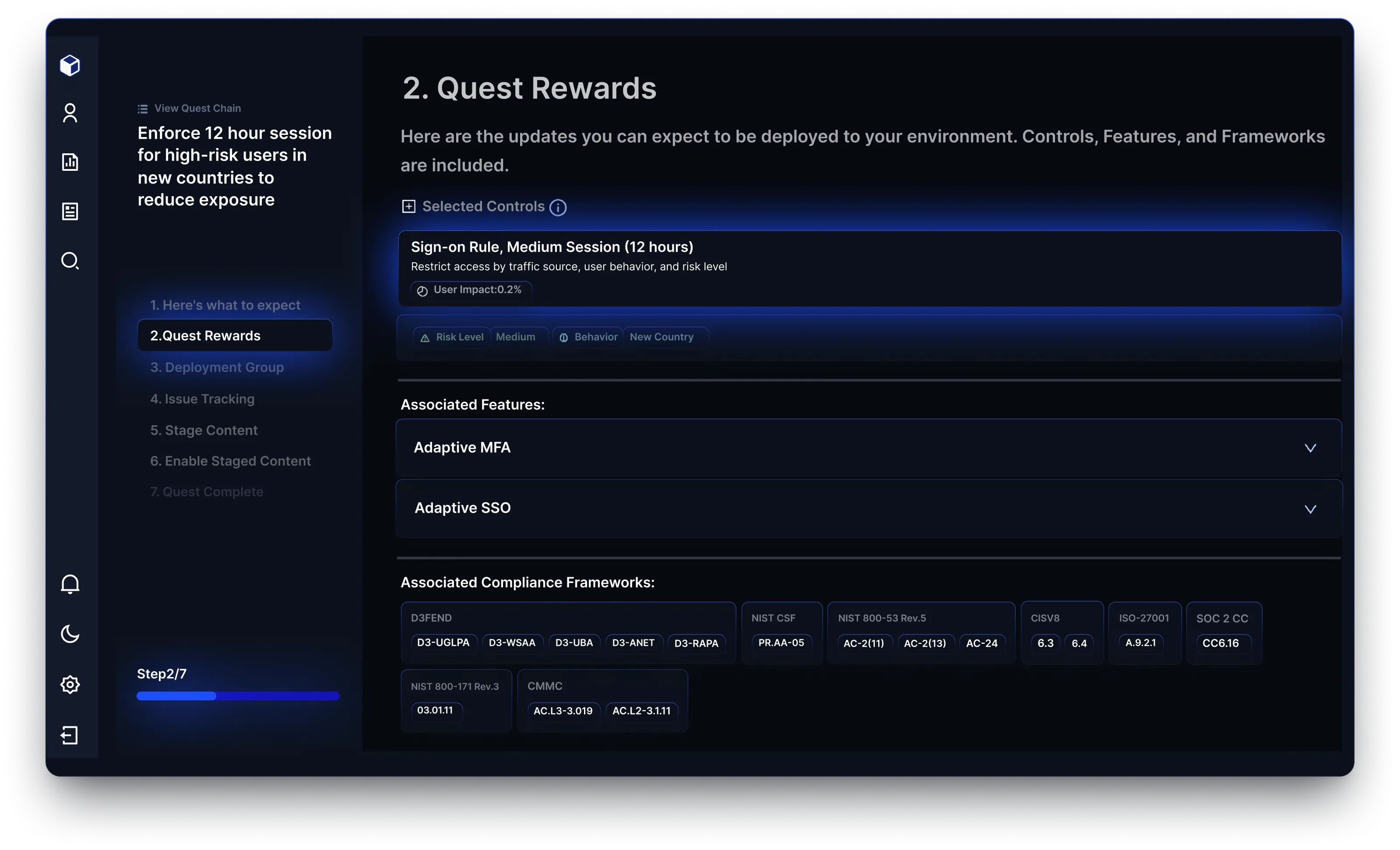
Reach designs optimal sign-on policies by leveraging real attack data and contextual risk attributes. It ensures strong baseline security for all users while applying stricter controls to high-risk groups, improving both security and user experience.

Even when organizations identify the right security policies, implementing them across IAM platforms can be complex and time-consuming. Manual policy adjustments lead to inconsistencies, delays, and misconfigurations.
Reach streamlines IAM security by providing one-click automation and detailed deployment guides. Security teams can efficiently stage and apply policy changes with precision, ensuring best practices are enforced without adding operational overhead.
Reach identifies and prioritizes exposure risks across email, network, endpoint, SaaS applications, and identity access management. By focusing on the most relevant threats, Reach helps organizations safeguard their most vulnerable asset: their people.
Reach automates remediation with context-driven recommendations, deployment guides, and change tickets tailored to your tools and environment. This ensures security changes are actionable, reducing the time and effort required to improve your security posture.
By connecting to existing tools, Reach provides a clear view of risk exposure, prioritizes based on your unique threat profile, and offers actionable insights. This approach empowers security teams to focus on what matters most, avoiding wasted efforts.
Unlike platforms that stop at assessments, Reach bridges the gap by guiding action. With deep integrations, automated prioritization, and tailored remediations, Reach enables organizations to reduce exposure and better utilize their existing tools.
To join the community of customers enjoying the benefits of Reach and learn more about how it can transform your security posture, visit: