New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowMicrosoft’s security suite offers extensive capabilities, but without proper configuration, critical protections can be overlooked. Organizations need a tailored, dynamic approach to fully optimize their security posture.

Lack of Visibility into Current Security Posture

Underutilization of Microsoft Security Investments

Uncertainty Around When to Upgrade to E5
Reach evaluates your existing E3/E5 environment, identifying how security features are currently used and uncovering opportunities for improvement.
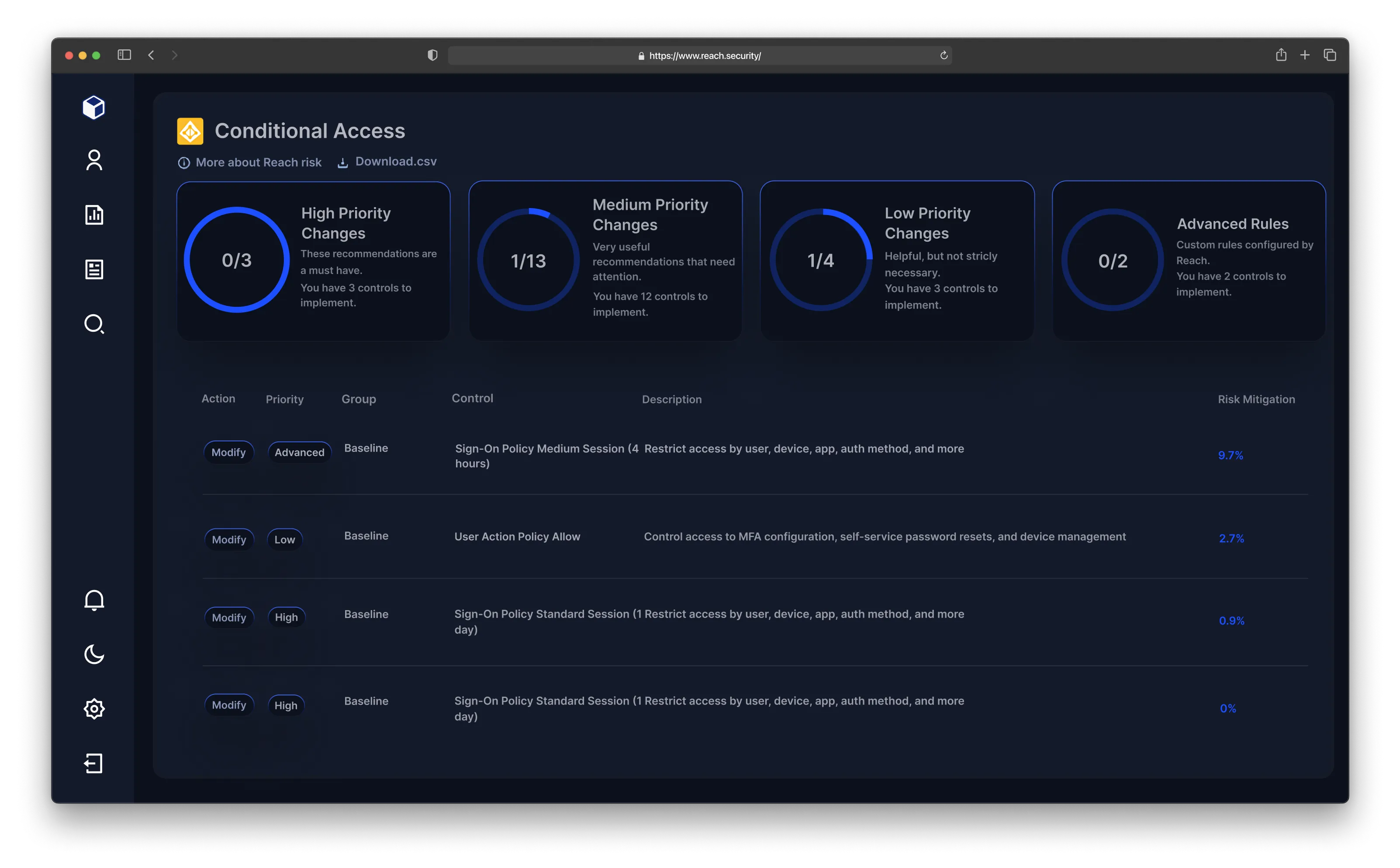
Many organizations lack visibility into how their Microsoft security features are configured, making it difficult to assess whether existing controls effectively mitigate threats. Without a clear view of security posture, teams may unknowingly leave critical gaps unaddressed.
Reach continuously evaluates your E3/E5 environment, analyzing configurations and identifying opportunities for improvement. By mapping security controls to real-world threats, Reach ensures you’re fully leveraging Microsoft’s built-in protections to strengthen your defense.

Microsoft’s E3 and E5 security tools offer extensive capabilities, but organizations often struggle to deploy the right features where they’re needed most. Without clear guidance, security teams may underutilize powerful defenses, leaving risk exposure unchecked.
Reach provides ongoing insights into your Microsoft security environment, helping you prioritize and optimize configurations to maximize your licensing investment. By aligning security controls with actual attack patterns, Reach ensures organizations get the most protection from the tools they already own.
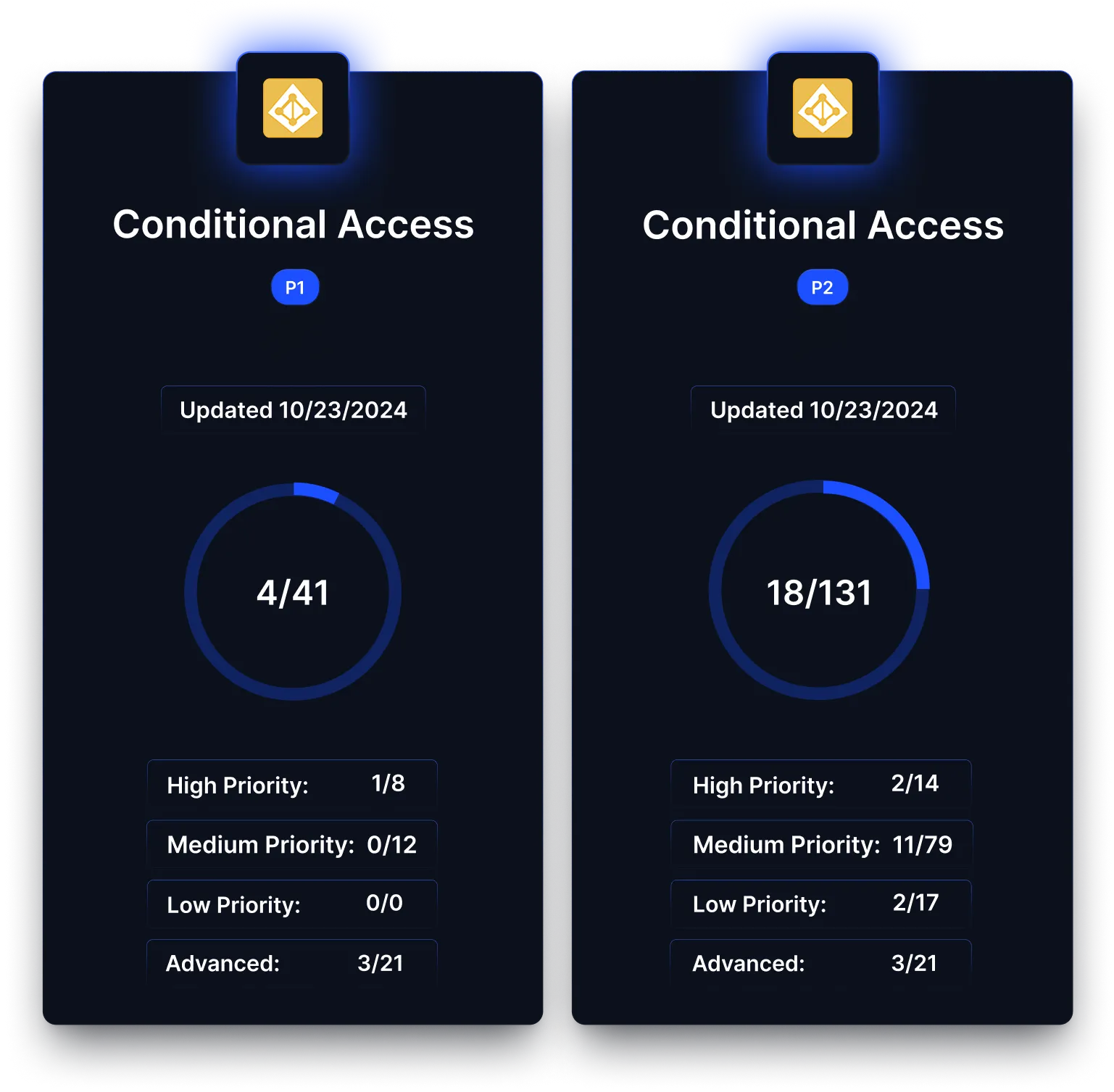
Deciding whether to upgrade to E5 can be challenging, as organizations often lack the data to determine whether the additional security features will deliver measurable value. Without clear evidence, upgrade decisions are either delayed or made based on guesswork.
Reach translates real attack data and security telemetry into actionable insights, demonstrating when and where E5 features would provide meaningful improvements. By quantifying risk reduction and security gains, Reach empowers organizations to make informed, justifiable upgrade decisions.

Reach identifies and prioritizes exposure risks across email, network, endpoint, SaaS applications, and identity access management. By focusing on the most relevant threats, Reach helps organizations safeguard their most vulnerable asset: their people.
Reach automates remediation with context-driven recommendations, deployment guides, and change tickets tailored to your tools and environment. This ensures security changes are actionable, reducing the time and effort required to improve your security posture.
By connecting to existing tools, Reach provides a clear view of risk exposure, prioritizes based on your unique threat profile, and offers actionable insights. This approach empowers security teams to focus on what matters most, avoiding wasted efforts.
Unlike platforms that stop at assessments, Reach bridges the gap by guiding action. With deep integrations, automated prioritization, and tailored remediations, Reach enables organizations to reduce exposure and better utilize their existing tools.
To join the community of customers enjoying the benefits of Reach and learn more about how it can transform your security posture, visit: