We’re thrilled to introduce the new Compliance View within Reach! Built to support Governance, Risk and Compliance (GRC) teams, Reach customers can now drill in to see how the configurations in their enterprise security products tie back into prominent GRC frameworks, and how they can use these products to improve their maturity with a given framework.

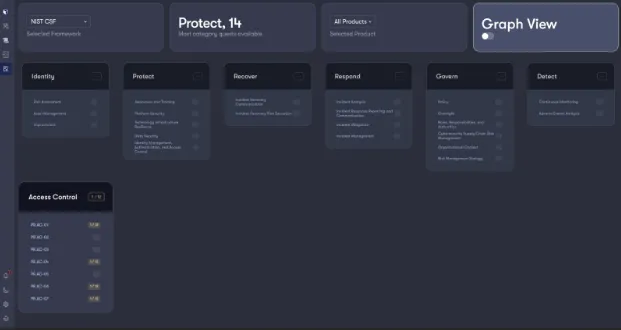
What’s New in the Compliance Tab?
We’ve expanded our capabilities to map security product controls to the following compliance frameworks:
- ISO 27001
- NIST Cybersecurity Framework (CSF)
- NIST 800-53 NIST 800-171
- SOC 2
- CIS Controls v8
- CMMC
- MITRE D3FEND

Why Compliance Matters
Governance, Risk, and Compliance teams are the unsung heroes ensuring organizations stay secure and meet regulatory standards. Their work directly impacts the bottom line and an organization’s ability to operate and generate revenue.
This new feature isn’t just about supporting security teams—it’s about enabling GRC teams to streamline their workflows, enhance collaboration, and provide verifiable proof of compliance based on the hard work of their security counterparts.

Customers of Reach are already taking advantage of the Compliance View to better understand how their enterprise security products can help boost their maturity for a given compliance framework. If you are a security leader looking to bridge the gap with your GRC counterparts, let’s talk!
Reach is the first purpose-built platform that closes the gap between assessing your security posture and reducing your exposure through operational changes using configuration guides, workflows, and automation - all contextualized and prioritized to maximize the efficacy of your existing tech stack. To learn more, visit reach.security/try-reach.










