The relationship between IT and security runs deep. IT focuses on enhancing business operations by optimizing processes and improving efficiency, while security implements protective measures across the network to ward off threats.
As organizations expand and evolve, the relationship between the two becomes equally as important as it is complex. The rapid pace of technology changes to drive revenue and streamline operations, coupled with an increasing number of sophisticated cyber threats, forces both IT and security teams to constantly adapt. This dynamic environment makes it challenging to maintain the integrity of security controls while ensuring operational efficiency and availability. For security teams, this challenge is especially evident when it comes to monitoring and maintaining established security controls from a configuration lens.
Security Prioritizes Controls; IT Prioritizes Availability
Security teams invest significant effort into deploying measures that protect users, networks, and infrastructure through a wide array of enterprise security products. However, there are instances where these measures may inadvertently impact business critical functions, and the deployed controls must be modified. For example, if a security policy causes a key executive to lose access to essential resources, IT (or a security colleague) might disable the control to restore access as soon as possible. While this achieves IT’s goal of maintaining availability, it also removes a safeguard designed to protect against potential threats. Meanwhile, the security team remains unaware that the control has been removed, and this lack of knowledge compounds with scale.
The Importance of Monitoring for Control Drift: A Practical Example
Consider a scenario where a security engineer implements a new sign-on rule in Okta, designed to log out highly targeted users, including the CFO, after one hour if they are logging in from a new device.
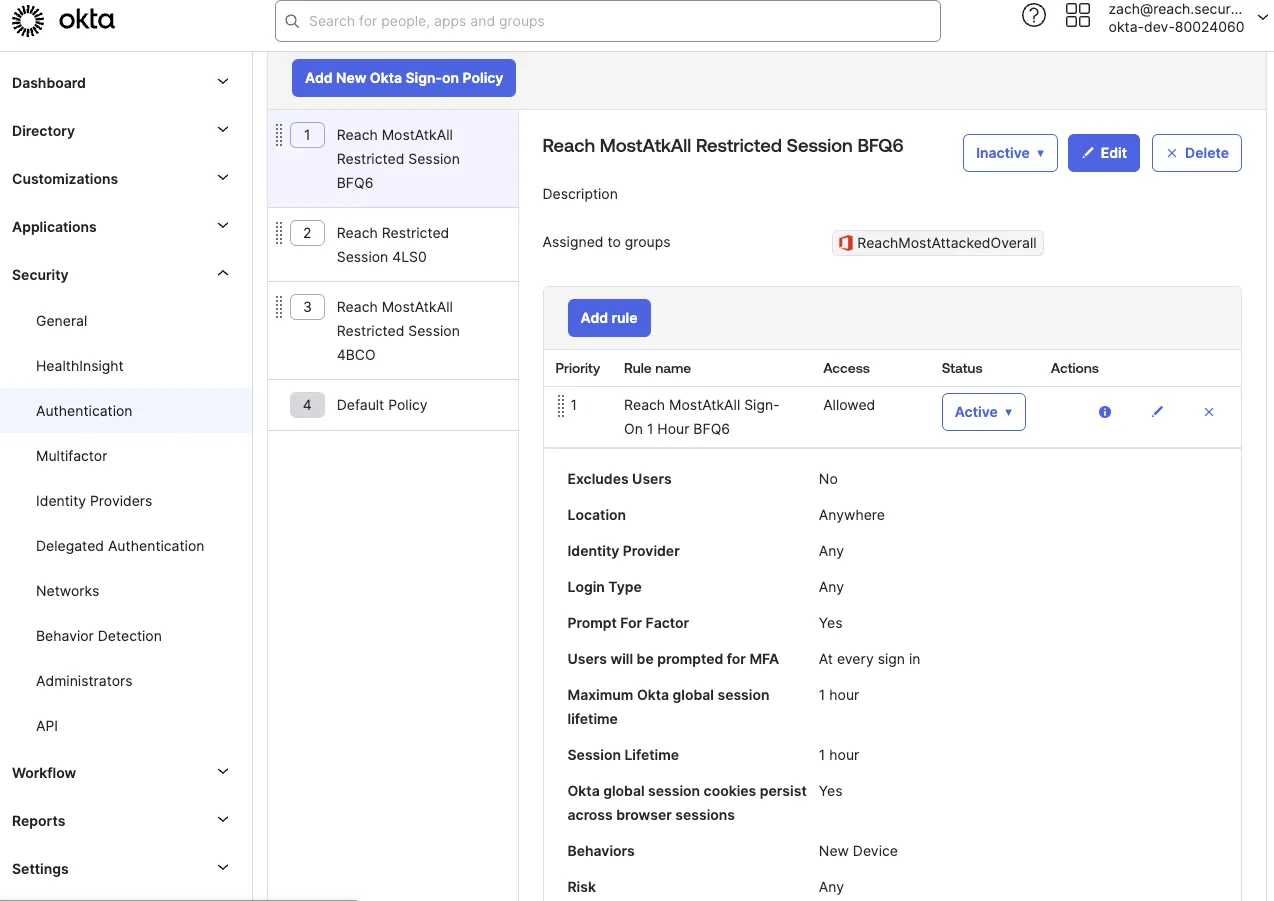
If the CFO, using a new laptop, is timed out while working on sensitive financial data, IT might disable the policy to prevent future interruptions, especially when the ask is coming from the c-suite.
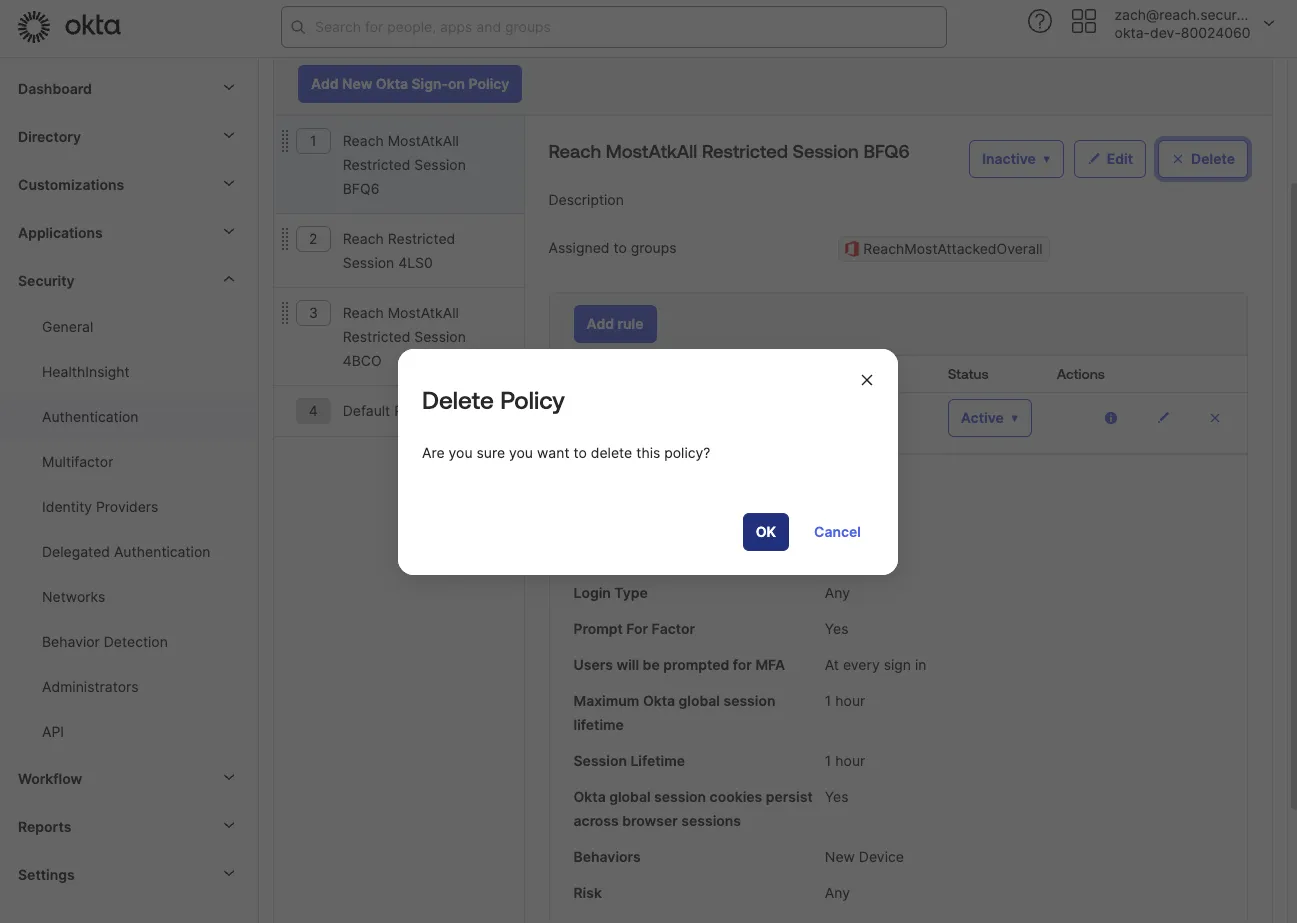
From a security perspective, this eliminates a critical control intended to address the downstream impact of credential compromise, as attackers will almost always be attempting login from a new device after getting a hold of credentials. To address this, security teams must continuously monitor configurations and controls to detect any deviations from the established baseline and take action when drift is detected.
Enter Reach
Beyond making recommendations, Reach creates an inventory of the configurations that have been deployed into your security products and tracks these deployments for changes over time.
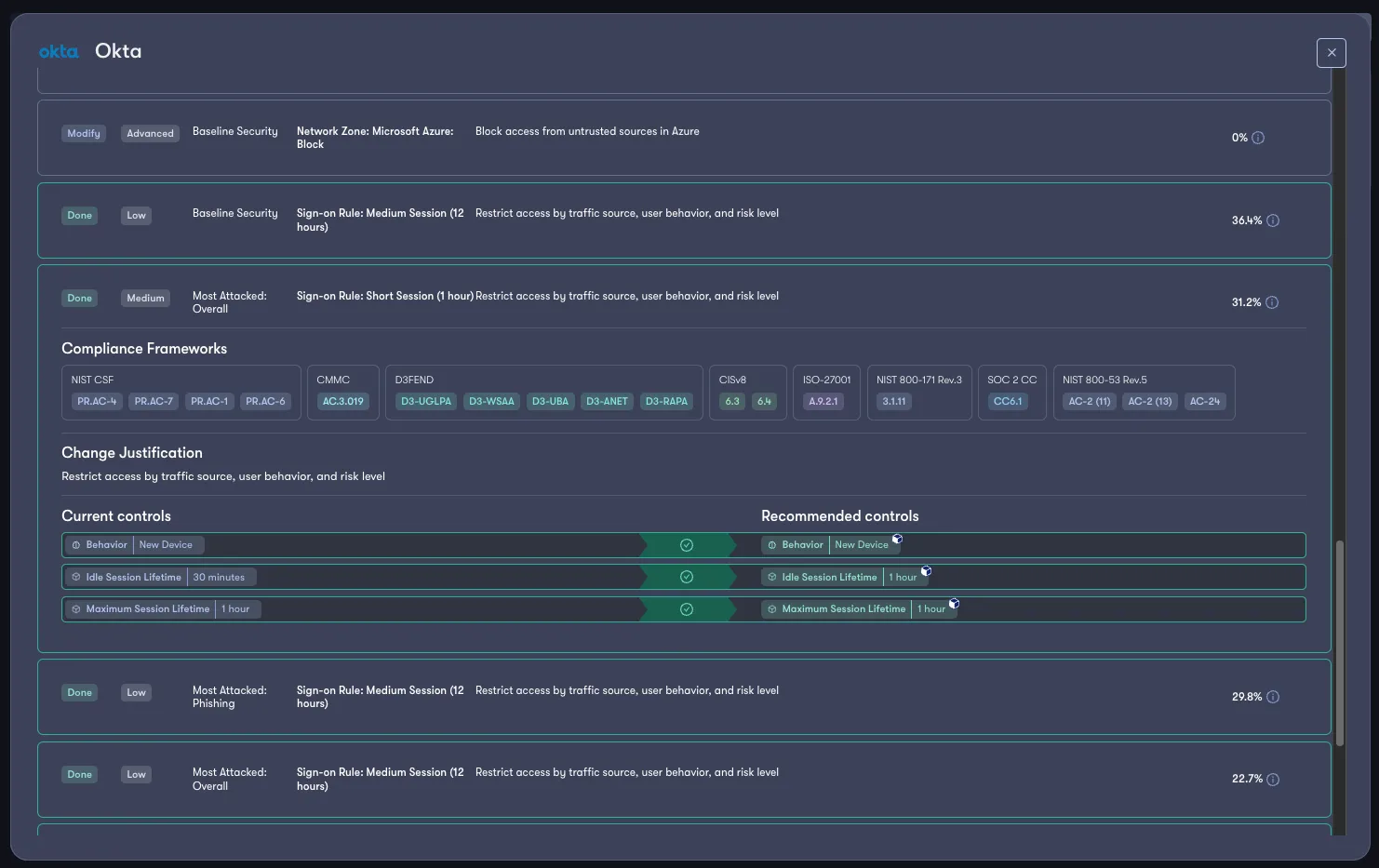
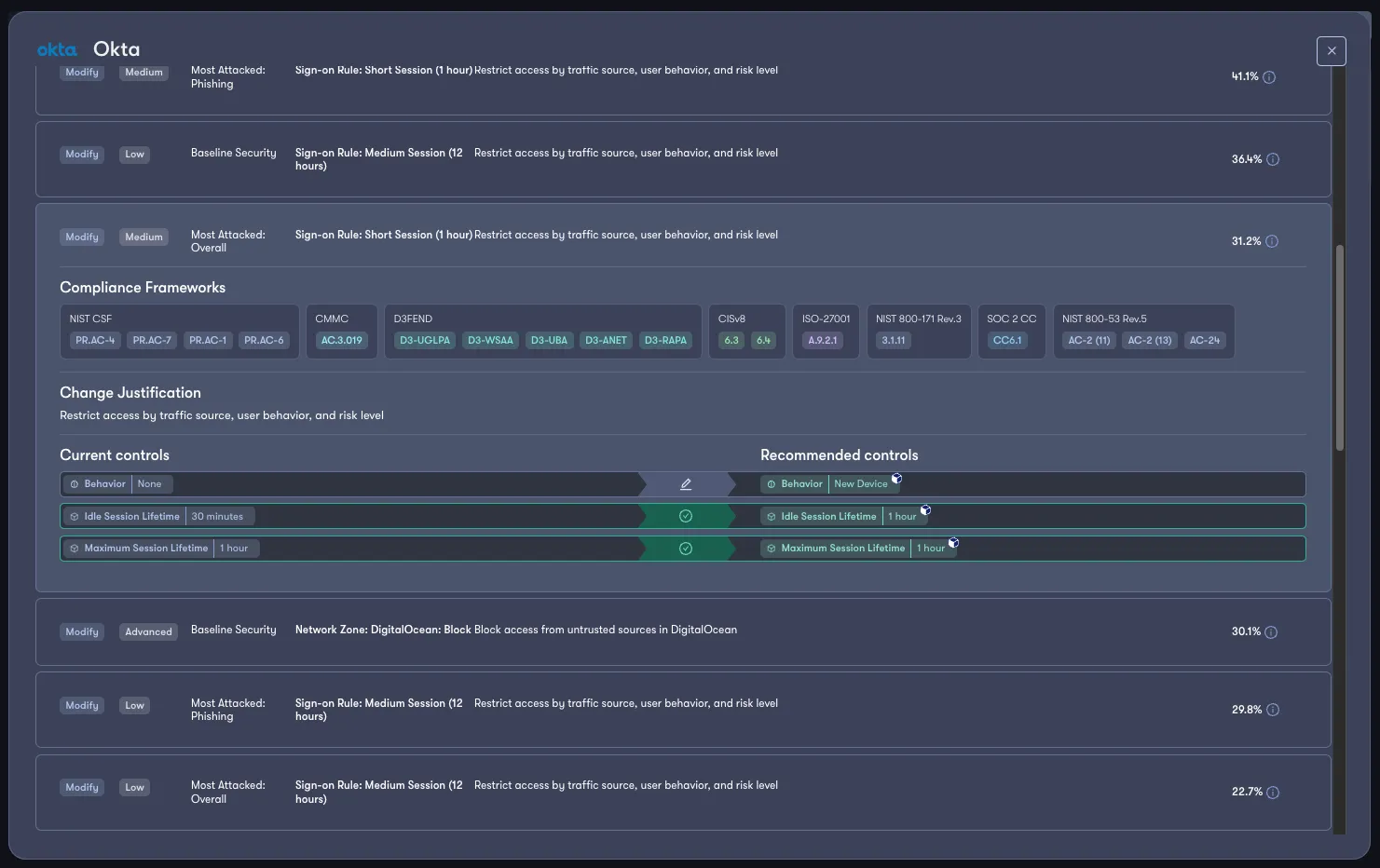
This allows you to proactively understand when changes to controls outside of your direct purview have been made, allowing you to act accordingly while maintaining a healthy level of availability without sacrificing security.
More About Reach Security
Reach is the first AI purpose-built to reprogram your security infrastructure based on who you are and how you're being attacked. Organizations of all sizes trust Reach to make mission-critical decisions because it doesn't hallucinate and it doesn't make mistakes. It's a different kind of AI. To learn more, visit reach.security/try-reach.










