Refreshed and updated September 10th, 2025.
Ready or Not: Credential Compromise Is Here in 2025
Identity-based attacks and credential compromise are here to stay. The 2025 Verizon DBIR reports that stolen credentials are the most common initial access vector, used in 22% of breaches, and 88% of “basic web application attacks” involve stolen credentials. Meanwhile, multiple industry trackers show a sharp rise in leaked credentials this year—Check Point observed a ~160% surge in compromised credentials in 2025—driven by infostealer malware and AI-scaled phishing. The reality is that you have to plan for when, not if, identity-based attacks and credential compromise will touch your organization.
“Start secure, stay secure, and prepare for new cyberthreats.” — Microsoft’s 2025 guidance for identity and access security.
Security Tools Optimization with Microsoft Entra ID Conditional Access
Microsoft Entra ID Conditional Access is a quintessential business enabler often relegated to an afterthought in security controls management. It enables IT to streamline business operations through SSO and app access. Yet, rich security authentication attributes frequently remain underutilized.
(Reader Note: While we focus on Microsoft Entra ID Conditional Access here, it’s important to recognize that similar considerations apply to other leading tools in the identity management space, such as Okta Adaptive MFA and SSO, Duo Security, ForgeRock, and Ping Identity. Each of these platforms offers unique features that enhance security and streamline access management, and they can be optimized in much the same way.)
To enhance your IAM security posture with Conditional Access, it’s important to fully understand the capabilities you’re licensed for, identify what’s currently being utilized, and leverage untapped features to mitigate risks.
Step 1: Confirm What You’re Licensed For (and What You’re Using)
Entra ID provides a broad set of sign-in signals and controls under P1 and P2. Common examples:
Examples of P1 Features:
- Session Controls: Reduce the default session time for added security.
- Named Locations: Implement policies based on the geolocation of sign-in attempts.
- User Actions: Enforce MFA checks following specific user actions, such as device registration.
- Phishing-Resistant MFA: Equip high-profile users, like administrators, with phishing-resistant tools such as YubiKeys.
Examples of P2 Enhancements:
- Includes all P1 features, plus:
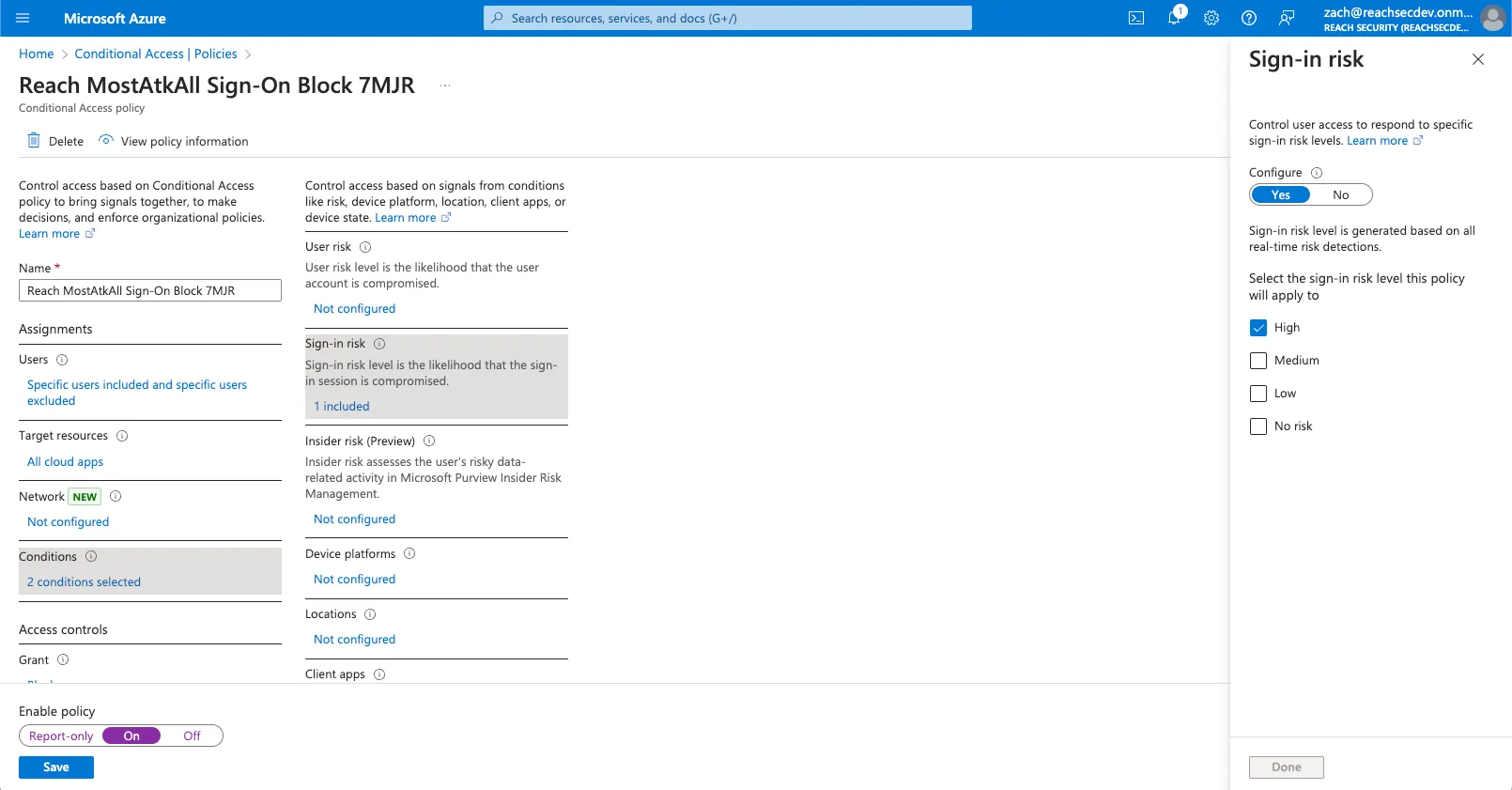
- User Risk: Assessed by Microsoft's threat intelligence to indicate the likelihood of identity compromise.
- Sign-in Risk: Also defined by Microsoft, indicating the authenticity of sign-in attempts.
Step 2: Model Licensed Capabilities to Address Risk Hotspots
After assessing available features, focus on those with the greatest potential to mitigate risks. This understanding can help advocate for the deployment of specific capabilities to IT or justify ROI from a risk reduction standpoint when considering license upgrades (e.g. P1 to P2).
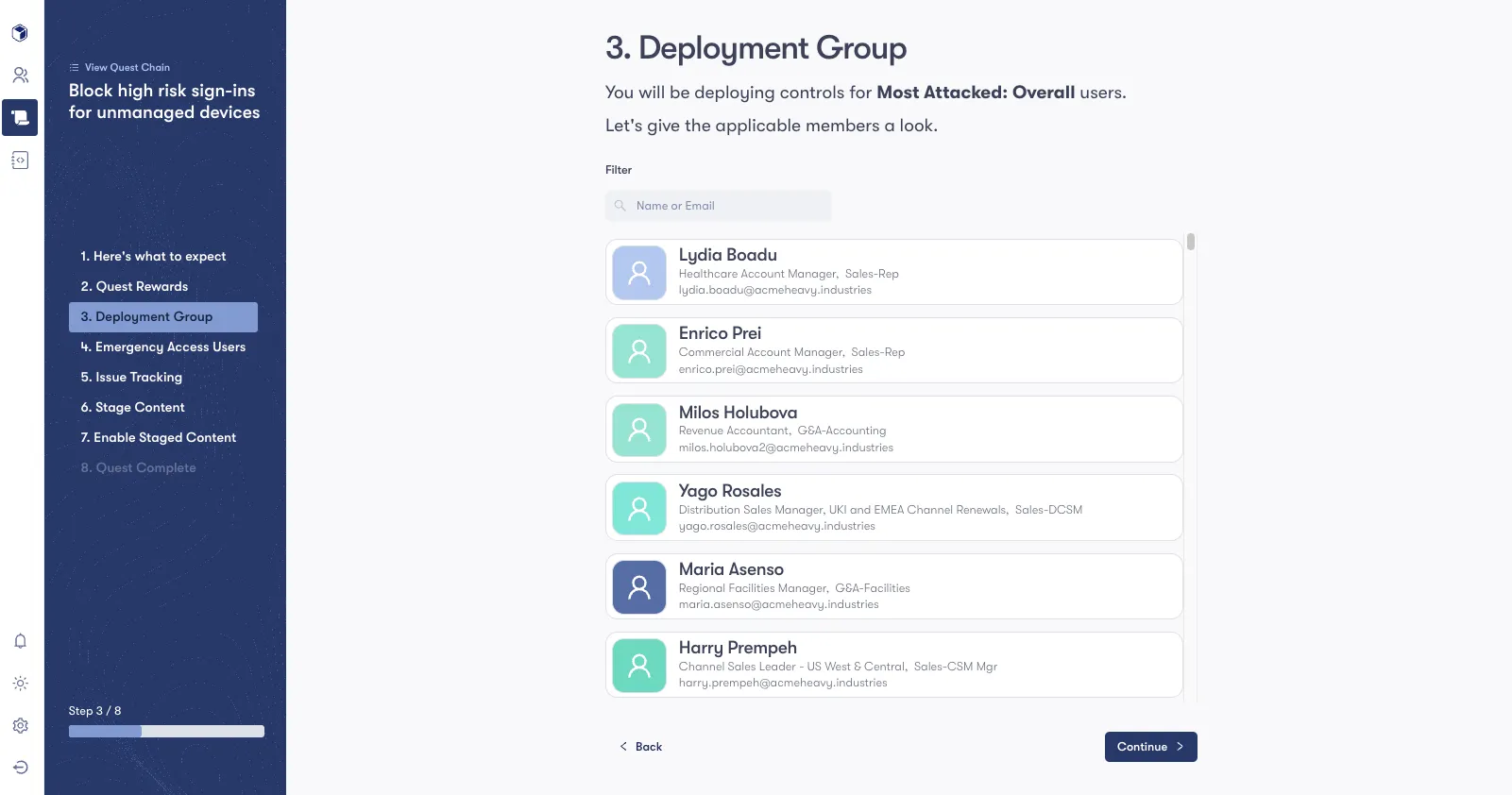
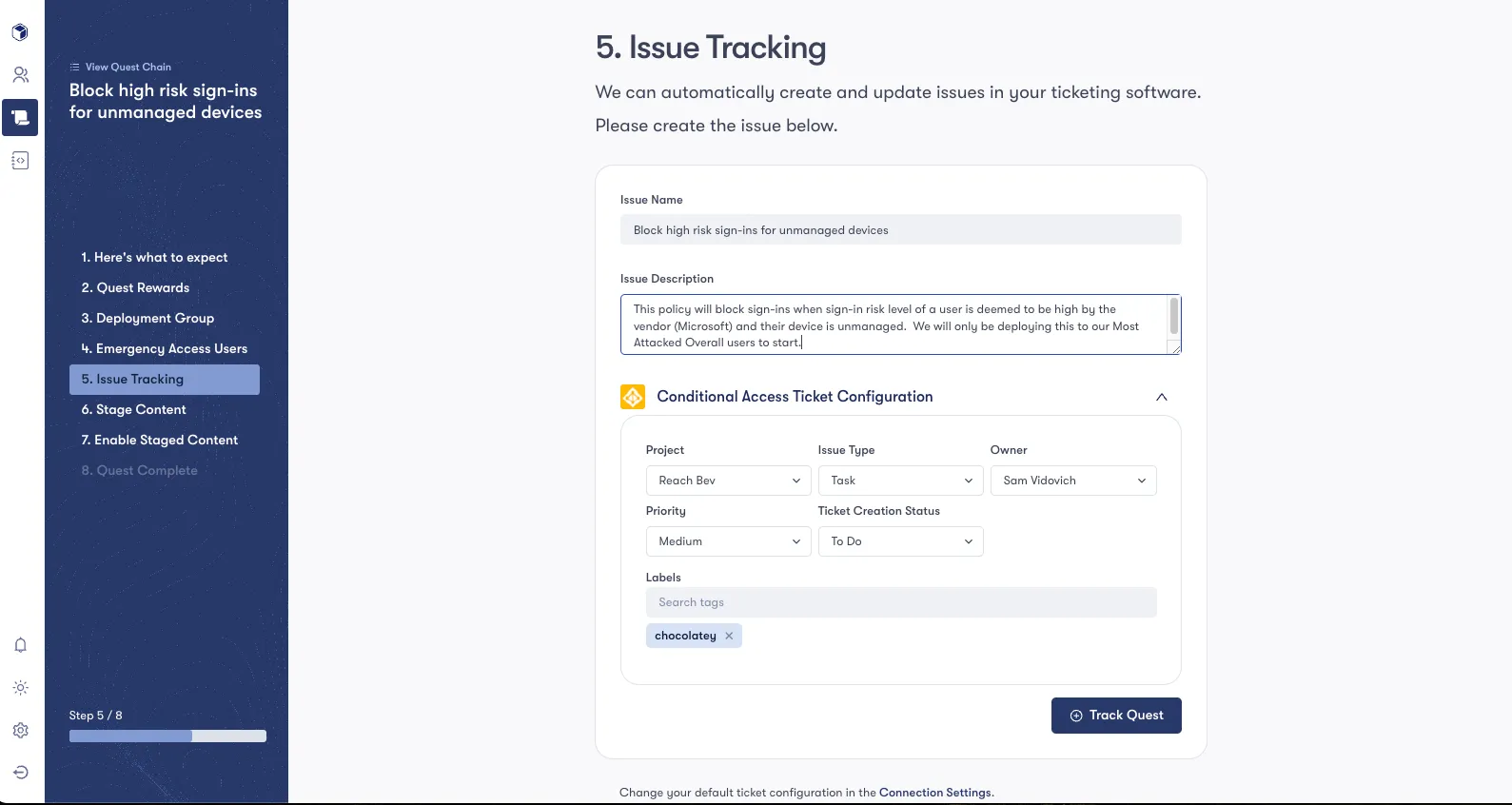
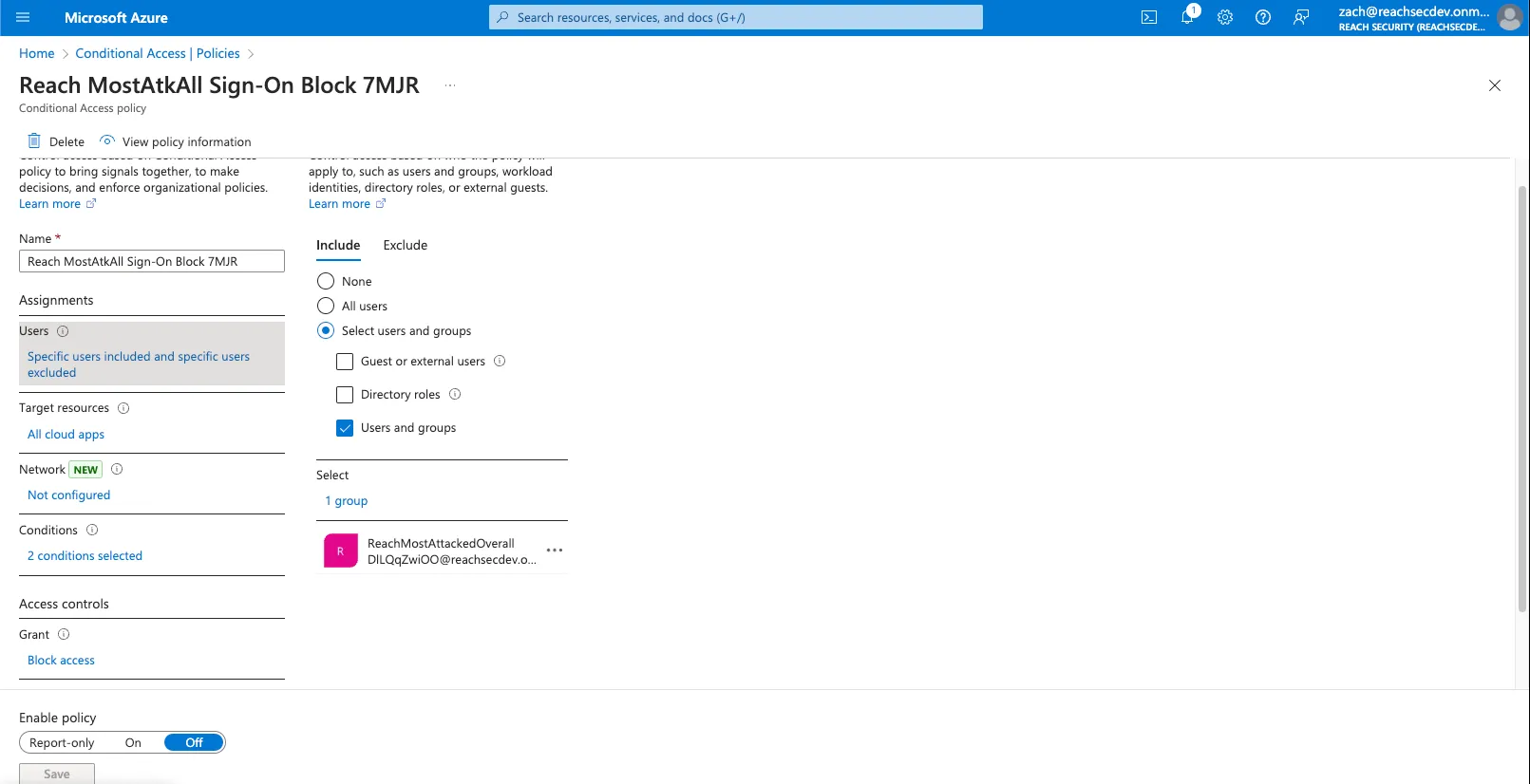
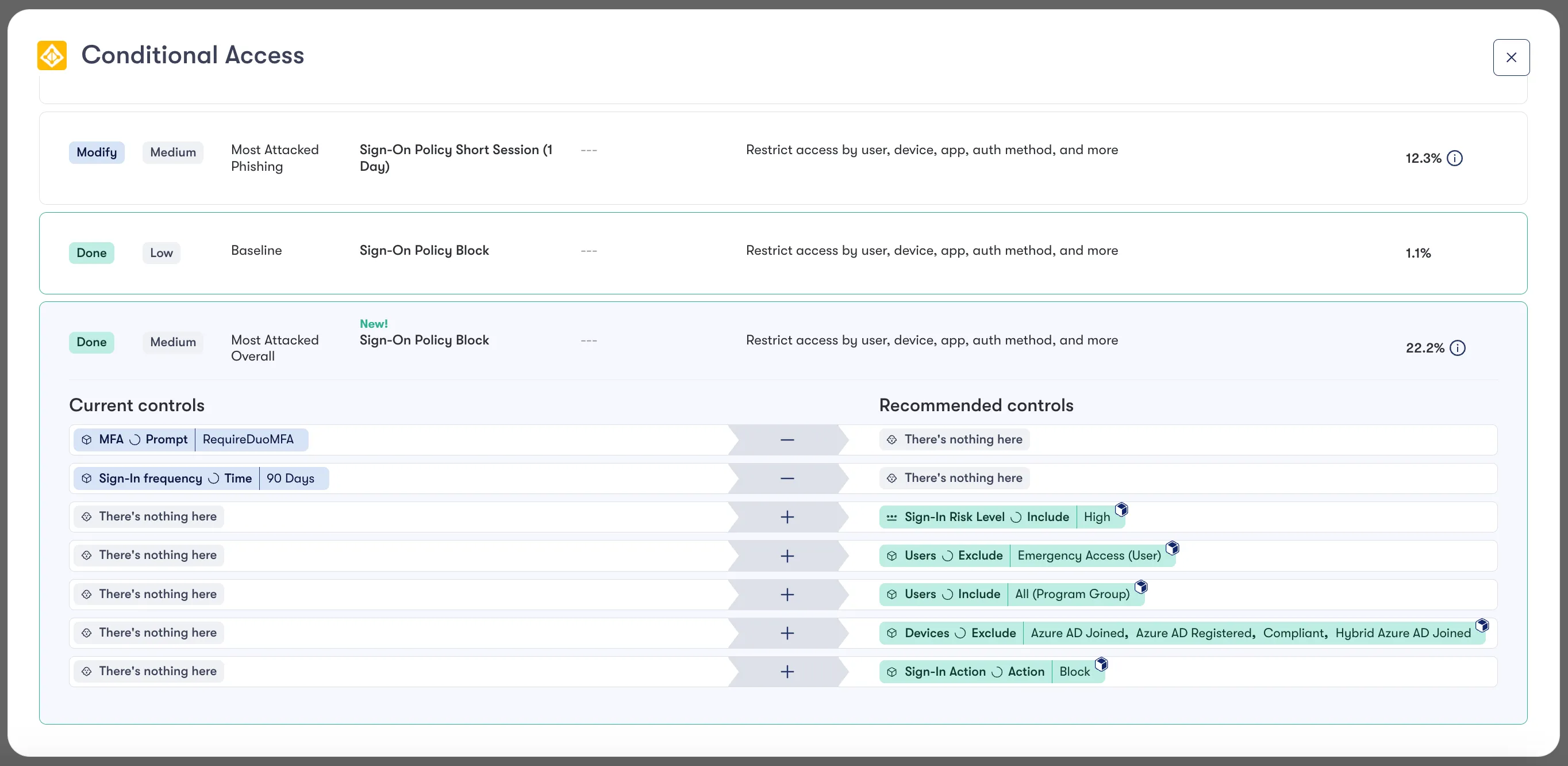
Step 3: Construct and Deploy Risk-Mitigating Sign-on Policies
Consider a scenario with a P2 licensed organization aiming to block high risk sign-ins for users that are disproportionately attacked, but only if their login originates from an unmanaged device.
- Identify high-risk users by analyzing varied security data sources like email, EDR, IAM and network logs.
- Monitor these users within Entra, noting changes over time.
- Implement a custom, risk-based sign-on policy for these users.
After taking care of steps 1 and 2 (covered in our identity-centric approach to Tools Rationalization blog) we can use automation capabilities in Reach Quests to action on deployment.


Conclusion: Assume Credential Compromise
Conditional Access contains simple yet powerful sign-on attributes that can be tailored to your business with a risk-based approach. Whether you're undergoing security tool consolidation efforts or embarking on an IAM hardening project, consider starting with a series of tailored sign-on policies that address risk where most breaches start.
More About Reach Security
Reach Security is the first platform that bridges the gap between knowing your exposure and actually fixing it. Security teams are overwhelmed by exposures from misconfigurations, vulnerabilities, and tool sprawl. Most solutions stop at reporting—Reach operationalizes remediation.
With Reach, organizations can:










