As we approach the end of the year and everyone starts to publish their annual year in reviews and top 10 lists, we at Reach decided to join in on the tradition and highlight some of the most common security misconfigurations that we've observed. Through collaboration among our teams, we've identified the top 10 misconfigurations that often slip through the cracks and significantly impact an organization's security.
Below we've outlined some of the most commonly missed or underutilized configurations, along with insights into why they matter and how addressing them can strengthen an organization's security posture.
- No Max Session Requirements
- Blocking Abused or Unused Networks
- Network Visibility (URL Filtering/SSL Decryption)
- Rule ordering on firewall
- Credential Phishing Detection
- MFA for Password Changes and Device Joins
- Not Fully Leveraging Custom Detections (STAR/IOA Rules)
- Relying on Default Policies
- Attachment Blocking for Unsafe File Types
- Unsecured Web Directories
While this post won't dive into every misconfiguration on the list, we'll highlight a few that are interesting from a defender's perspective. By addressing even a few of these items, organizations can further enhance their resilience against threats facing their organization.
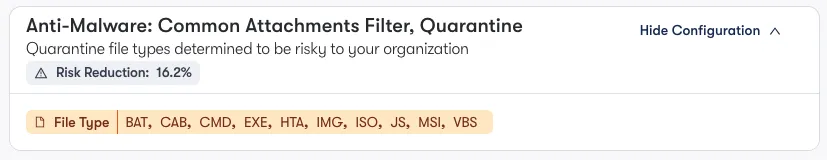
Attachment Blocking For Unused File Types
Every security team has faced pushbacks on blocking specific file types at some point. Blocking well-known file types like .exe or .sh is often easy to justify, but other types such as .pdf may require additional checks to avoid interrupting business workflows. Recently, there's been a rise in spear-phishing attacks using RDP files, underscoring the need for consideration of policies blocking based on attachment types.
Reach helps by analyzing data from email security gateways to better understand the types of malicious emails being delivered to users at your organization. By using this data about the types of threats being sent to users and the associated malicious file types, Reach makes it easier for teams to prioritize attachment blocking decisions that best protect users and align with real-world threats.
Underutilized Custom Detections (STAR/IOA Rules)
Configuring custom activity rules on your endpoint security tools provides better visibility into an attacker's intent and behavior and gives insight into threat patterns that provides added context outside of regular IOC's. However, it can be difficult to strike a proper balance as too many additional rules can overwhelm security teams with more work and more alerts to follow up on.
Reach simplifies this by ingesting attack data and recommending optimal configurations for endpoint tools, not just using the features of the platform but also providing other rules that can be actioned to identify and contain malicious behavior. This data-driven approach refines how these rules are applied and helps security teams correlate data across tools and enact defensive measures that address threats across the company.

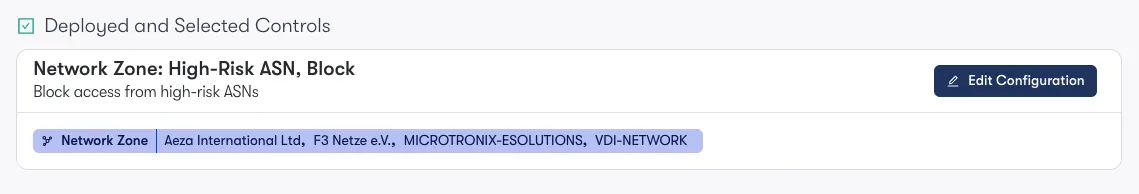
Blocking Abused or Unused Networks
Blocking malicious traffic from networks that do not have any business value is often overlooked but can significantly reduce the logs and alerts that a security team must manage. Although these attacks may come from less sophisticated actors, they create potential footholds for a group that can later sell access to a network to more sophisticated actors.
Reach simplifies this by identifying these networks by monitoring failed authentication attempts from untrusted sources and highlighting them. This visibility enables teams to take quick action and block potentially harmful networks before they become a greater risk.
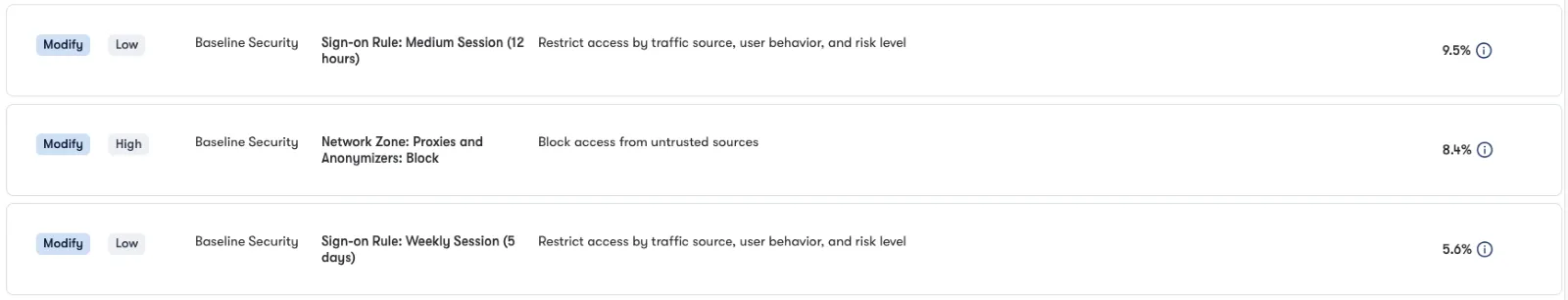
No Max Session Requirements
When deploying IAM policies, organizations often overlook options for more granular control over session limits. While many organizations set broad policies and perhaps a few for high-risk logins, additional controls are available to enhance the user experience and adjust session durations based on the specific risk level of each sign-in.
Reach assists by analyzing existing policies and providing insights on optimizing IAM configurations. For example, low-risk sign-ins could be granted additional access to productivity features like password resets which risky logins from new devices or countries might have shorter session limits set in order to mitigate any potential risks.
If you're familiar with some of these misconfigurations and are looking for proactive ways to identify them and other areas for improvement, sign up for a free tools rationalization assessment to receive tailored recommendations.
Reach is the first purpose-built platform that closes the gap between assessing your security posture and reducing your exposure through operational changes using configuration guides, workflows, and automation - all contextualized and prioritized to maximize the efficacy of your existing tech stack. To learn more, visit reach.security/try-reach.










