Credential compromise is a beachhead for high-profile attacks, making user authentication more critical than ever. IAM tools like Okta offer powerful ways to combat this risk, but fully optimizing your licensed capabilities can be a lengthy and challenging process.
Beyond risk, contextual, and behavioral based sign-on attributes included in the adaptive feature set, an often-overlooked component within Okta are network zones. Network zones provide a dynamic way to track IPs affiliated with a particular geolocation – both physical (e.g. country) and in the cloud (e.g. IPs affiliated with cloud providers).
Let’s dive into how the latter is a powerful way to thwart advanced techniques used by attackers once credentials are compromised.
The Challenge of CSPs in Cybersecurity
The shift to the Cloud brings many ways to access free trials of Cloud Service Providers (CSPs). Just about any provider will offer a trial license to entice businesses to build on their platform. While access to these free trials enable innovation, it also provides a means for attackers to spin up servers and anonymize the geolocation of their malicious activity.
Read more: IP Spoofing In and Out of the Public Cloud
When it comes to sources of authentication attempts, tracking known-bad (or out of policy) providers becomes imperative when applying guardrails on access to your environment, as these providers are often the first place attackers will go to spoof their location.
But, IPs affiliated with these cloud providers are ephemeral in nature and constantly changing. So, how do you track a target that’s moving?
Dynamic Network Zones in Okta – Tracking and Blocking
Statically assigned IP based block policies affiliated with CSPs can become outdated fast. If you were to deploy a series of IPs affiliated with a known out of policy provider today, they’ll likely change tomorrow. This, after all, is the nature of how CSPs work. When it comes to tracking, manual maintenance of these lists impossible to do at scale. That’s where Okta and Reach come into play.
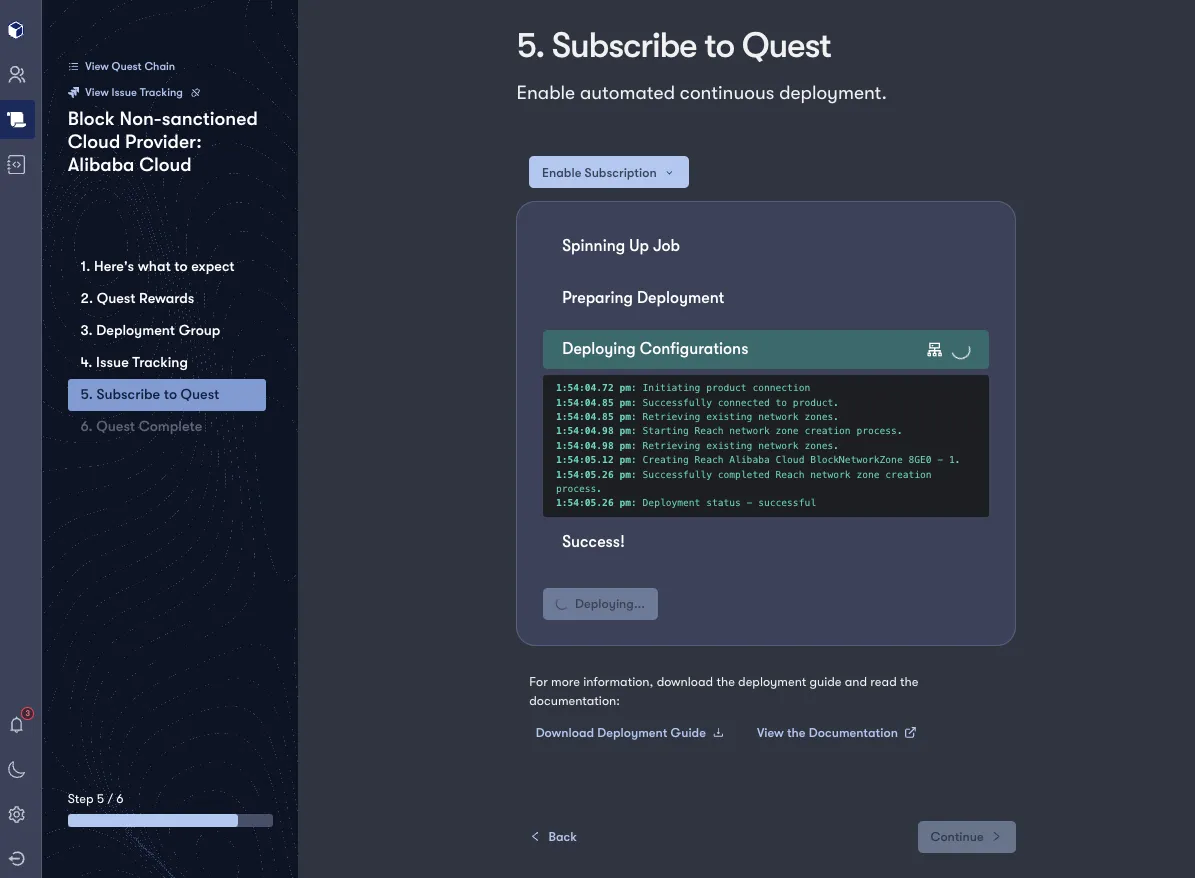
Reach addresses this pivotal vector by analyzing sign-on logs to spot nefarious login attempts from unfamiliar or unsanctioned CSPs. Let’s say 99.8% of your organizations sign-in attempts in the last year originated from AWS and Azure, and .2% originated from Alibaba Cloud or Tencent (and failed with high risk level assigned to the login attempts by Okta). Reach identifies this nuance in sign-in data and creates a recommendation to block login attempts originating from both Alibaba Cloud or Tencent moving forward, utilizing Network Zones in Okta as the means house these IPs.

Integrated Intelligence
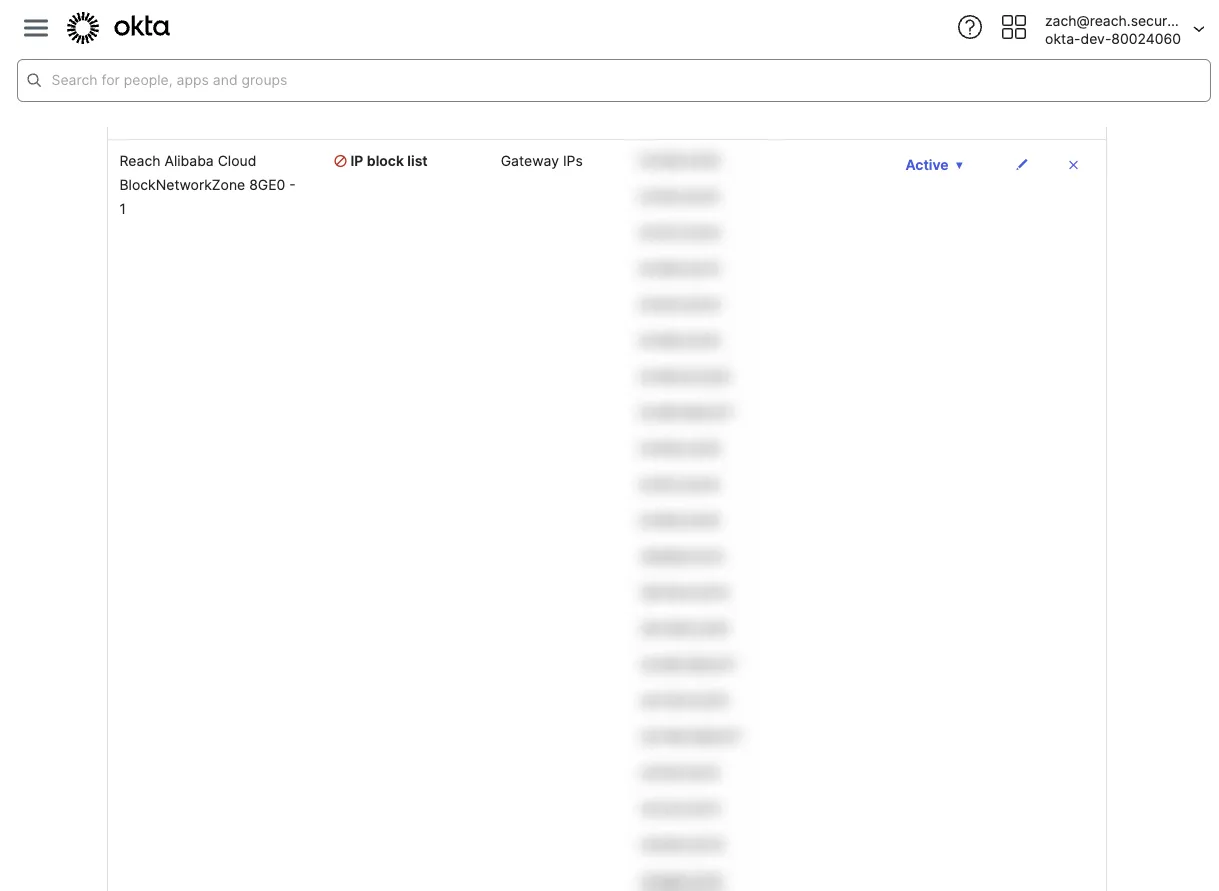
Reach’s dedicated threat research team maintains intelligence that tracks IPs affiliated with these known-bad providers and constantly updates these curated Network Zone(s) in Okta to allow you to stay on top of the known-bad CSP’s IP space. This intelligence, built and maintained by systems in-house by Reach, is curated for your unique deployment of Okta and integrates seamlessly, with updates to addresses pushed dynamically as IPs affiliated with these CSPs evolve overtime. Reach will also construct a block policy that references these dynamic Network Zones, allowing you to not only monitor the moving target, but action on it.
Conclusion: Strengthening IAM Security with Reach and Okta
Integrating Reach with Okta is a game-changer for boosting your security in the event of credential compromise. With Reach’s advanced analytics and proactive recommendations, organizations can better defend against threats from attackers looking to spoof their location and gain access to sensitive infrastructure. This combo not only maximizes the value of Okta’s Adaptive features, but also adds an extra layer of security for a more comprehensive approach to your IAM deployment.
More About Reach Security
Reach is the first AI purpose-built to reprogram your security infrastructure based on who you are and how you're being attacked. Organizations of all sizes trust Reach to make mission-critical decisions because it doesn't hallucinate and it doesn't make mistakes. It's a different kind of AI. To learn more, visit reach.security/try-reach.










