One of the key value propositions of Reach is that our platform not only increases your security posture by providing critical insights, but it also allows customer to take action and deploy configurations with automation. This is typically referred to as the “last mile” in the process and within Reach they are deployed as to what we refer to as Quests.
One exciting recent development by our team is the ability to tailor Quests during deployment and make modifications afterward. This enhancement is critical to the deployment process, enabling Reach to meet customers where they are in their automation journey by gradually implementing configuration changes and adapting to their business needs and security challenges.
Below is a walkthrough of an example of a tailored Quest. The example customer scenario is that:
- They utilize AWS cloud services within North America only
- They leverage Okta and AWS authentication requests should never happen outside of North America
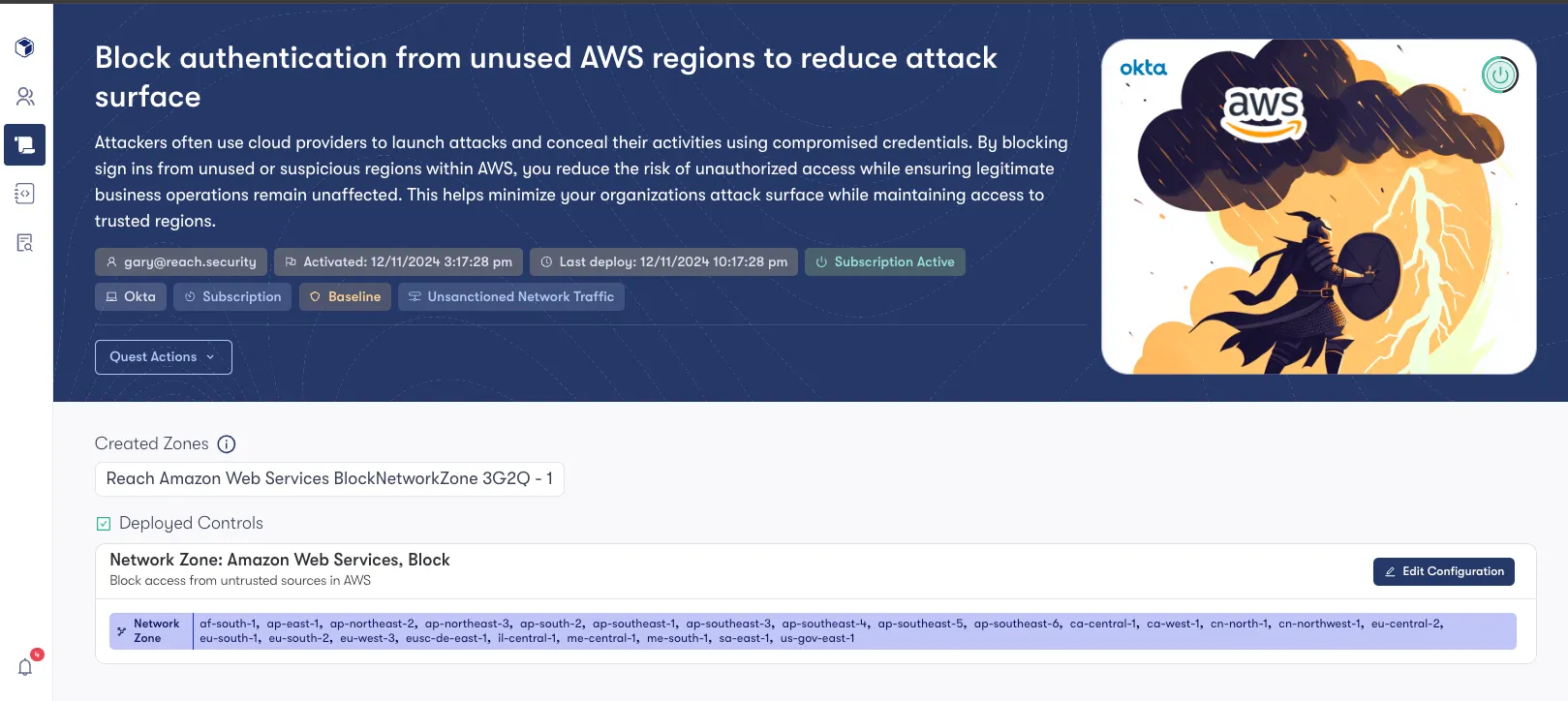
Bad actors often try to evade detection by spinning up trial instances across various cloud providers to launch their attacks. Controlling unsanctioned cloud activity is, therefore, an effective way to reduce an organization’s attack surface. Since this customer operates exclusively within North America, Reach has automatically generated a Quest to block authentication requests from outside these regions, categorizing them as “Unsanctioned Network Traffic” (as shown in the image below). Another key advantage of Reach is its ability to maintain IP/ASN intelligence across multiple cloud providers.
Next, within this Quest, we can view the details of the Network Zone that will be created and blocked within Okta. Notably, Reach has identified AWS authentication requests from within North America as normal behavior, so they are excluded from this configuration. Only regions outside North America are included. However, during the initial deployment, the configuration can be easily adjusted by selecting “Edit Configuration” to add or remove any AWS regions as needed.

Lastly, once deployed, Reach provides a full audit trail that this Quest has been deployed within the environment, as shown in the image below.
Finally, the business landscape has shifted, and the company has decided to expand operations into Europe. To accommodate this, authentication requests from those regions will need to be permitted. No need to worry—simply select “Edit Configuration” in the Quest, as shown above, to make the necessary adjustments.
We will simply deselect the EU AWS regions listed below, and the Quest will then update the Network Zone and block within Okta to remove these regions, thus permitting authentication requests from AWS EU regions.
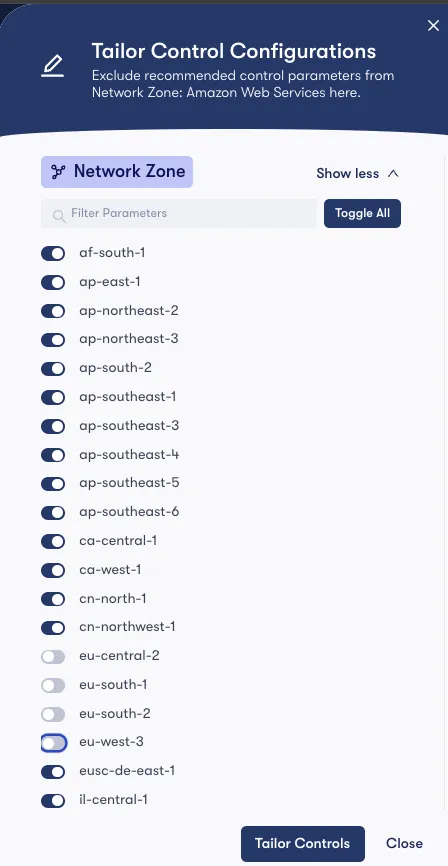
Lastly, the Subscription has been updated, and we can now see those regions as “Deselected Controls”.

In summary, Reach empowers our customers to implement changes within their environments while offering the flexibility to adapt to their unique environment, specific threat profiles, and business needs.
Reach is the first purpose-built platform that closes the gap between assessing your security posture and reducing your exposure through operational changes using configuration guides, workflows, and automation - all contextualized and prioritized to maximize the efficacy of your existing tech stack. To learn more, visit reach.security/try-reach.










