Staying ahead of adversaries is a constant challenge due to the evolving tactics and techniques that they leverage to gain access and achieve their objectives. While frameworks like MITRE ATT&CK have become an industry standard for understanding and discussing adversary behaviors, it can be challenging for defenders to map their own defenses. MITRE D3FEND, however, was built for defenders to provide a common language and a structured approach to planning and implementing defensive measures.
In the last blog, we looked at how to operationalize MITRE D3FEND. In this post, let’s explore why it’s exciting for defenders and how Reach can help identify exposure gaps and modify policies to better protect against the latest threats.
What Is MITRE D3FEND?
MITRE D3FEND is a complementary framework to MITRE ATT&CK, but instead of focusing on attacker TTP’s, it is designed to help provide better insights into defensive techniques. These measures are categorized to help organizations understand how to best counter specific threats.
For example, if an attacker is leveraging credential dumping as identified by T1003 in MITRE ATT&CK, D3FEND maps out defensive techniques like Mandatory Access Control for hardening, and leveraging Decoy Credentials for detecting the activity. This bridges the gap between attacker activity and how an organization can respond to these threats. The beauty of this framework lies in its practicality and its ability to help organizations identify not only strengths in current tools, but also gaps that can be improved.

Why is D3FEND Interesting to Defenders?
1. Shifting from reactive to proactive. Typically, security measures are very reactive, whether reviewing alerts in a SIEM, or investigating suspicious activity on a given endpoint after it occurs. D3FEND helps organizations become more proactive by highlighting preventative measures that can be implemented.
2. Better communication amongst teams. Security teams often struggle to justify investments in security tools or align on internal strategies. D3FEND provides a clear framework for communicating not only what threats exist but also how to address them, which can be invaluable when building a security roadmap.
3. Aligning defensive measures to real-world threats. The framework ties defenses directly to the tactics and techniques used by adversaries. This makes it easier to prioritize resources and focus on defenses that counter the most relevant threats to your organization.
4. Complementing Compliance Frameworks. While frameworks like NIST CSF or CMMC focus on governance and compliance, D3FEND provides the technical detail necessary to operationalize those requirements.Together, they bridge the gap between meeting regulatory obligations and implementing actionable, effective defenses.
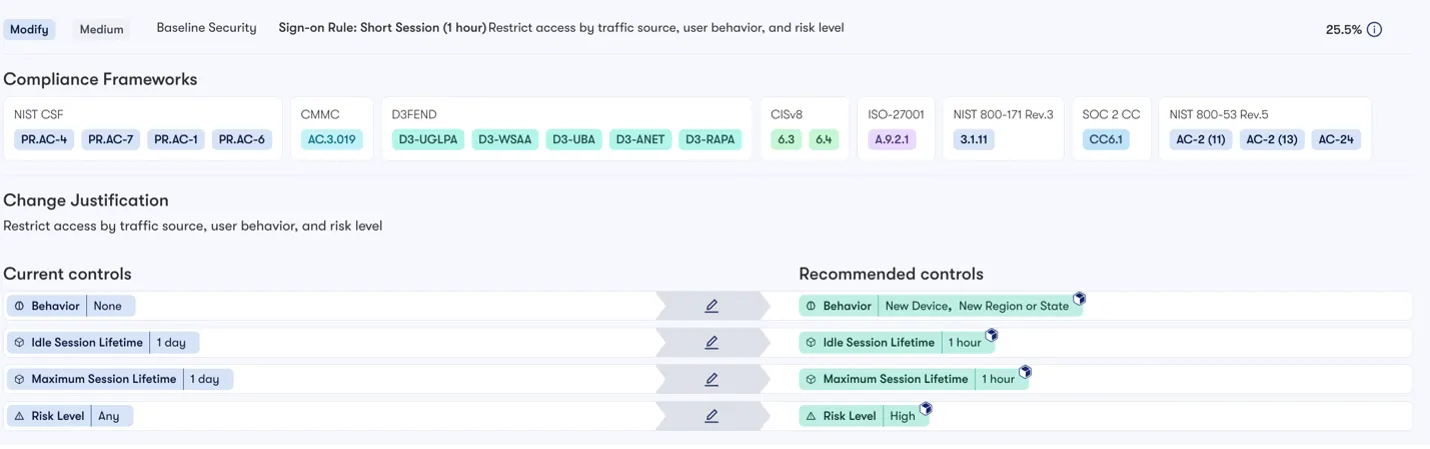
How Reach Security Helps
Reach Security operationalizes D3FEND by mapping its defensive techniques to your existing tools and identifying gaps in your configurations. Whether it’s improving Okta’s MFA policies, optimizing CrowdStrike’s endpoint protection, or ensuring Palo Alto’s SSL decryption is configured correctly, Reach ensures that your defenses align with D3FEND’s best practices.
By pairing D3FEND with compliance frameworks, Reach Security provides organizations with a comprehensive roadmap to achieve both regulatory compliance and robust, proactive defenses.
Reach is the first purpose-built platform that closes the gap between assessing your security posture and reducing your exposure through operational changes using configuration guides, workflows, and automation - all contextualized and prioritized to maximize the efficacy of your existing tech stack. To learn more, visit reach.security/try-reach.










