Beginning in October, Microsoft will mandate multi-factor authentication (MFA) for multiple Azure components, including the Entra admin portal. Given Microsoft’s research indicates that MFA can prevent over 99.2% of account compromise attempts, this is great news! For those utilizing Entra Conditional Access to govern how users authenticate to mission-critical applications, there are additional measures you can take within Entra to further reduce the risk of credential compromise. Let’s explore some strategies to elevate your Conditional Access implementation beyond MFA using the features you’re licensed for.
1) Risk Based Policies
In Entra, you can combine MFA with risk-based authentication attributes to manage user sessions. You have the option to select from two different risk levels:
- User Risk: Assessed by Microsoft's threat intelligence to indicate the likelihood of identity compromise.
- Sign-in Risk: Also defined by Microsoft, indicating the authenticity of sign-in attempts.
Once these risk levels are assigned there are a series of actions you may consider to augment MFA. For example, if the user risk level is medium or high, you may want to enforce a password reset after successful MFA, as Microsoft defines these risk levels as having a higher likelihood of account compromise.
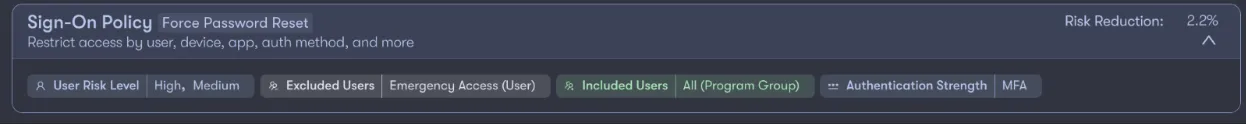
On the contrary, you may choose to block access entirely if the sign-in risk level is high and the device used for the authentication attempt is not joined or registered to the domain. In this scenario, MFA would not apply due to the context considered for the user’s login.
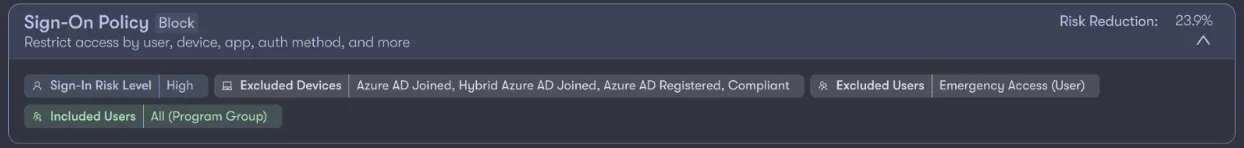
With Reach, you can take this one step further by tailoring these policies to individual users or groups based on their unique risk profiles. This ensures your highest-risk users are receiving the strongest protections that are dynamically adjusted as their risk level changes.
2) User Actions
In addition to applying MFA at login, you may want to enforce MFA when users perform certain actions that could amplify the impact of a credential compromise. Entra refers to these as user actions, and you can require MFA for actions such as changing MFA settings, resetting the account password, or joining/registering a device. These are often the first targets attackers go after when they successfully compromise credentials and gain access.

In this example, users would be prompted for MFA if they attempt to reset their MFA configuration or password while using a device that isn't domain-joined. For users trying to join or register their device, MFA should be required regardless of the device they are using.
If you’re not already using MFA for user actions, Reach can help you mobilize these changes by providing step by step deployment guides and ticketing automation through Reach quests.
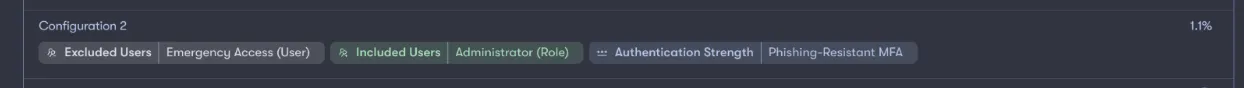
3) Phishing-resistant MFA
Implementing phishing-resistant MFA can be challenging to roll out across the entire organization. Therefore, you might consider starting with users who have the highest level of access, such as your admins. This approach enhances security for those with the most critical permissions, going beyond the basic requirements that Microsoft has set forth.
Closing
Regardless of Microsoft’s upcoming requirements, it’s important to remember that the bare minimum may not be enough to fully secure your organization.
With Reach, you can continuously validate Conditional Access settings to ensure they remain effective as your organization and its risk landscape evolve. Reach’s real-time monitoring ensures your MFA and other security controls adapt to new threats and changes within your organization without compromising legitimate users' login experience. For more details on how Reach can help you automate this entire process, check out or security optimization spotlight on Entra Conditional Access, where we dive into the details. Happy MFA’ing!










