For years, cybersecurity has lived under a grim banner: “It’s not a matter of if you’ll be breached, but when.”
That phrase became the industry’s guiding principle. Relying on prevention alone was slowly written off as impossible. Instead, the dominant wisdom declared that organizations must accept compromise as inevitable and prepare to deal with attackers after they had already gained a foothold.
This mindset reshaped cybersecurity investments and the technologies that emerged. It pushed the focus into the “post-breach” world, or what we like to call “right of boom”.
The Rise of Post-Breach Security
As the industry embraced the inevitability of breaches, investment and innovation surged into tools that could detect, investigate and respond (TDIR) once an attacker was already inside. Security teams adopted SIEMs to collect massive volumes of data. EDR tools tracked endpoint activity for signs of compromise. SOAR platforms automated incident workflows. And now, XDR solutions aim to connect it all together.
These technologies are powerful and play an important role. They’ve enabled organizations to investigate intrusions faster, automate aspects of response, and build a clearer picture of threats. Billions of dollars have been poured into this space, and the message is consistent: if you can detect fast enough and respond effectively, you can contain the damage.
The Spiral and the Squeeze
But ultimately, this model doesn’t scale. Every new attack vector spawns a new defensive tool. New attack vector? Add another tool. New tool? Hire more people to run it. Every new tool added to your stack requires more people and resources to manage it. Over time, security teams find themselves in a doom spiral, buried under sprawling toolsets, each with its own dashboards, alerts, and configurations to manage. Every tool demands expertise, constant updates, and ongoing tuning.
You thought the spiral was bad. Make way for the “squeeze”. While tools pile up, threats keep evolving—never slowing down long enough for teams to catch up. On one side, security teams are pressured to keep up with the constant churn of product releases and feature updates across dozens of platforms. On the other, they’re inundated with a relentless stream of new threat intelligence they must interpret and defend against. The result? Security teams are squeezed in the middle, spread thin, spending their days in reactive mode—racing from alert to alert, update to update—with little time to proactively shore up their defenses.
This reactive treadmill doesn’t just burn out teams. It leaves organizations exposed in exactly the ways attackers expect.
The Opportunity: Exposures
The truth is that most breaches don’t occur because attackers are impossibly sophisticated. They succeed because defenses are weakened by preventable exposures: misconfigured tools, drift in security settings, and unused features that could block attacks if they were enabled.
Think about it: identity systems with overly permissive accounts, firewalls with forgotten rules, endpoint platforms missing critical controls. These aren’t exotic zero-days. They’re simple cracks in the armor that build up over time as environments grow more complex. And attackers are opportunists—they go after the weakest link.
I get it. No one wants to work on misconfigs. It’s not sexy. It’s boring. But closing gaps and eliminating exposures is one of the fastest ways to substantially reduce risk. Detection and response platforms are invaluable once something goes wrong, but they don’t shut the open doors that attackers use to get in. Without addressing exposures, organizations are left in a constant state of vulnerability—no matter how advanced their detection stack might be.
Stop the Spiral and Relieve the Squeeze
Reach is designed to stop the spiral and relieve the squeeze security teams face. Instead of focusing only on what happens after an incident, Reach shifts the focus to pre-event. By minimizing exposures, you can compliment and maximize the power of your right-of-boom security investments. Now, security teams can be both proactive and reactive, strengthening their defenses and eliminating exposures before they can be exploited.
By deploying AI agents for security architects, Reach enables proactive security that identifies exposures, prioritizes action, guides remediation, and continuously validates your security posture. With Reach, security teams can move from reactive firefighting to proactive defense.
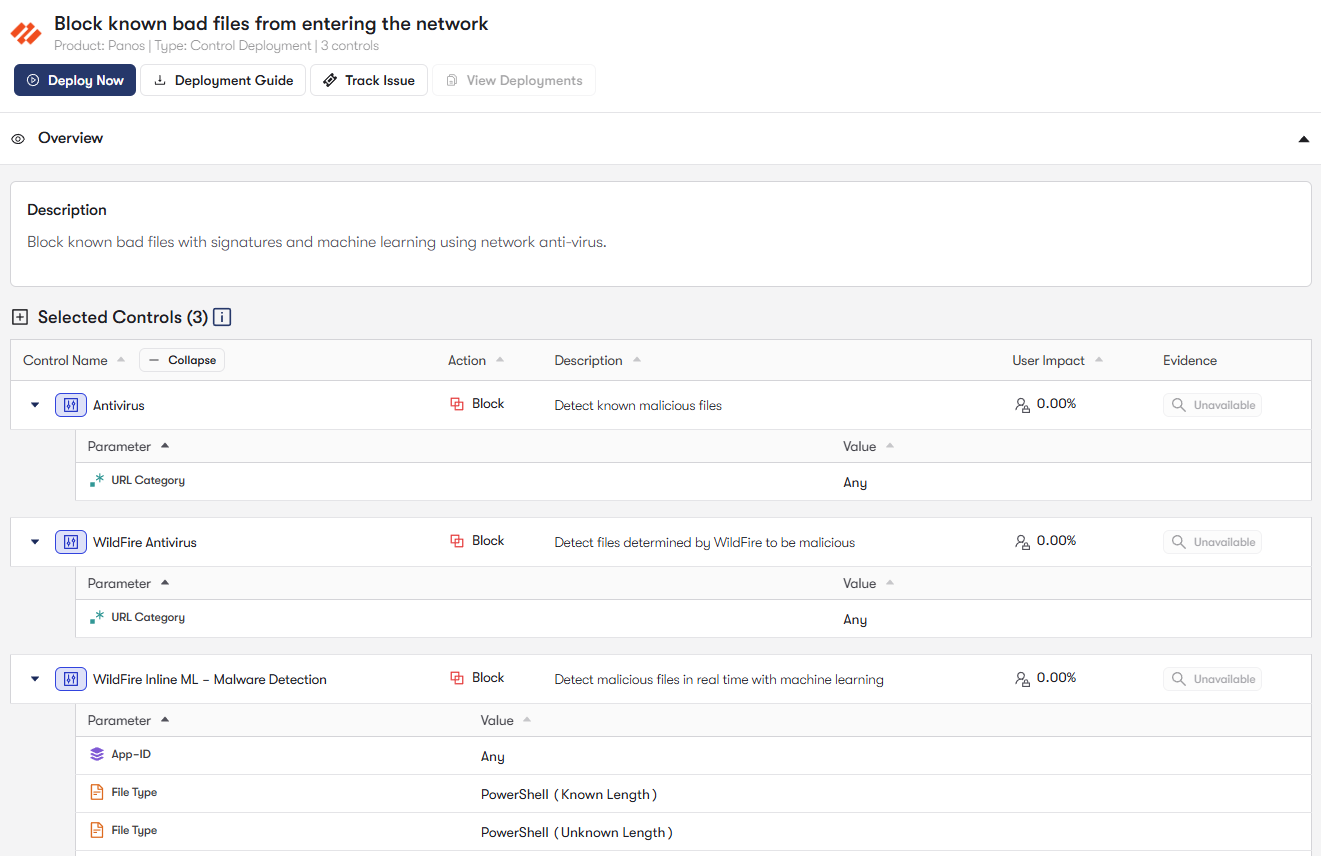
Identify Exposures from Misconfigured and Underused Tools
Exposures are the gap between your existing security posture and controls, and the ever-evolving sophisticated attacks that target you. Whether because of misconfigured security tools or underutilized capabilities across identity, email, network, or endpoint security, this creates critical gaps that attackers can exploit.
Reach uses multi-model AI to automatically reveal hidden exposures, misconfigurations, and underused controls at machine-speed. Reach’s MastermindAI™ connects directly to your existing identity, endpoint, email, firewall, SASE, and directory services. Using domain-specific language models that uniquely understand what these tools are capable of (and configuration detail), MastermindAI™ analyzes millions of data points across your environment to understand how effectively your defensive controls are being used – and misused – across your people, assets, and systems. Reach marries this precise analysis with a deep understanding of real-world security data and up-to-date threat context. This unique understanding of both attacker techniques and your defensive controls allows Reach to proactively pinpoint exposures and provide a comprehensive understanding of risk across the organization.
Prioritize Action Based on Real-World Risk
Modern threat exposure management tools surface issues and generate reports and assessments, but often lack the context to prioritize what matters and enable action. This leaves teams stuck with more data, not more clarity on how to proceed.
Reach prioritizes action to reduce the most risk in the shortest amount of time. Reach AI agents prioritize based on the reachability of a vulnerability, attack behaviors, and configuration context. It also aligns control recommendations to your organization’s priorities. This helps you focus on the controls that truly eliminate exposures, reduce risk, and improve the return on your existing security investments.
Guide Remediation to Rapidly Boost Security Posture
Most exposure assessment platforms identify vulnerabilities and misconfigurations, but they fall short of enacting the changes needed to eliminate these exposures. Security teams are already stretched thin, overwhelmed with manual investigations and manual remediation tasks, and unable to take on more workload.
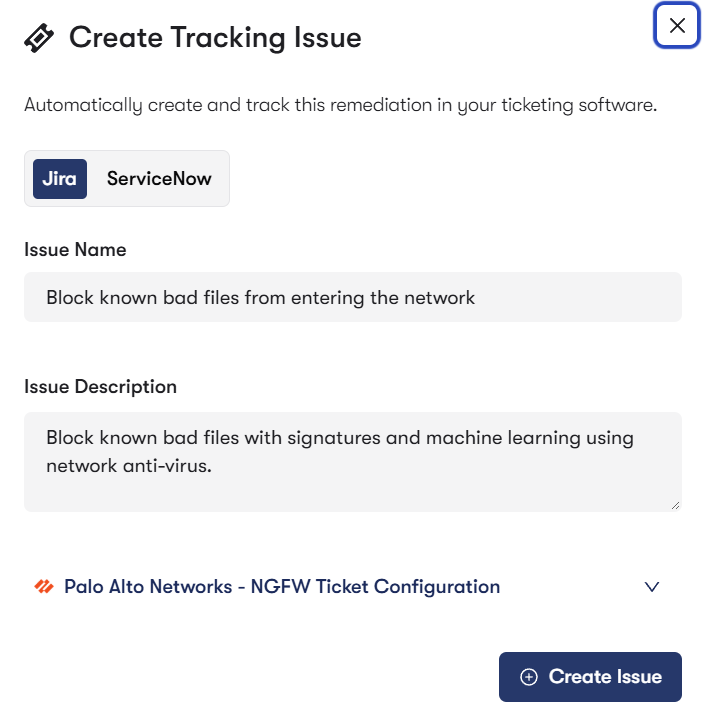
Reach doesn’t just surface risk – it fixes it for you. Reach AI agents generate detailed configuration guides with context-aware recommendations and step-by-step fixes. Reach then executes tailored remediation workflows—aligned to industry standard frameworks like MITRE and NIST—across your security ecosystem through direct integration with your ticketing systems, including ServiceNow and Jira. That being said, Reach gives you options. You can utilize the configuration guide to walk through the steps and push the changes manually; leverage our integrations with ticketing tools to automate the ticket creation and assign the work to your IT team; or automate the configuration change into a staged environment so your team can verify it before pushing it live. Pick the approach that works best for you. This allows your team to quickly deploy changes and close gaps without adding friction to existing processes, or adding more manual task workloads to your already overworked team.
Continuously Validate That Controls Stay Aligned to Threats and Policy
Security posture isn’t static. Configuration drift quietly undermines even the best security plans, introducing risk as systems evolve and settings shift.
Reach AI agents, powered by ConfigIQ Drift, continuously monitor your configurations to detect drift the moment it happens. Reach validates that controls are working as intended, and ensures your defenses stay aligned with your evolving environment and threat landscape. Stay ahead of change and ensure posture isn’t just assessed – it’s maintained.
Need clarification about an exposure? Want to understand your risk profile in plain language? Need to create a custom drift rule to close gaps and maintain security posture? Just ask our AI agent Reacher™ for help to summarize results, answer questions, and deploy fixes and execute remediation tasks across your ecosystem.
From Buzzword to Backbone: AI at Reach
AI has become one of the most overused terms in cybersecurity marketing. Too often, it’s tacked on as a buzzword – a thin layer washed on top of tools, with little real impact. At Reach, AI isn’t an add-on. It’s the architecture and engine at the heart of how we solve problems.
At the core of Reach are AI agents designed to work like real teammates for security architects—not just generic copilots. These agents take on the heavy lifting across the four critical functions of security operations: identifying exposures, prioritizing what matters, guiding remediation, and continuously validating defenses. They don’t just generate alerts; they actively drive action and resolution.
Multi-Model, Domain-Specific Intelligence
Reach doesn’t rely on a single large language model bolted onto a product. Instead, we use multi-model AI, including domain-specific LLMs (DS-LLMs) trained on security configurations, real-world threat data, and attacker behaviors. Our MastermindAI connects directly into your security stack—identity, endpoint, email, firewall, SASE, and more—so it not only understands the tools you have, but also how effectively they’re configured and where they’re falling short.
This isn’t generic AI trying to make sense of your environment. It’s purpose-built intelligence, capable of analyzing millions of data points across people, assets, and systems to pinpoint exactly where exposures live and how they can be eliminated.
From Data to Decisions, Insight to Action - AI That Fixes, Not Just Flags
Most tools leave teams buried under raw data. Reach transforms that data into decisions. By combining configuration insight with attacker context, Reach prioritizes exposures based on real-world risk. Then, it guides you from insight to action—generating step-by-step configuration changes, automating remediation workflows, or even deploying fixes directly.
The industry is full of tools that detect problems but leave the burden of fixing them squarely on your team. Reach is different. Our AI agents generate context-aware fixes, map them to standards like MITRE and NIST, and integrate seamlessly into ticketing systems like ServiceNow and Jira. You decide the level of automation, but the power to close gaps—not just identify them—is built into the platform.
Continuous Validation with ConfigIQ Drift
Modern security programs rely on a suite of tools - EDR, IAM, email security, firewalls - owned and operated by cross-functional teams. While this shared responsibility model brings flexibility, it also introduces operational risk: configurations change constantly, are left untouched in the event of break-glass situations, and changes are rarely communicated in real time. Over time, security posture erodes and risk increases as systems change and configurations slip. This “configuration drift” quietly undermines even the best security plans.
Reach ConfigIQ Drift™ detects drift the moment it happens, helping you stay aligned to policy, prevent regressions, and fix issues before they become exposure. ConfigIQ Drift continuously validates that defenses remain in place and aligned with evolving threats. Instead of a static assessment, you get ongoing assurance that your environment is protected.
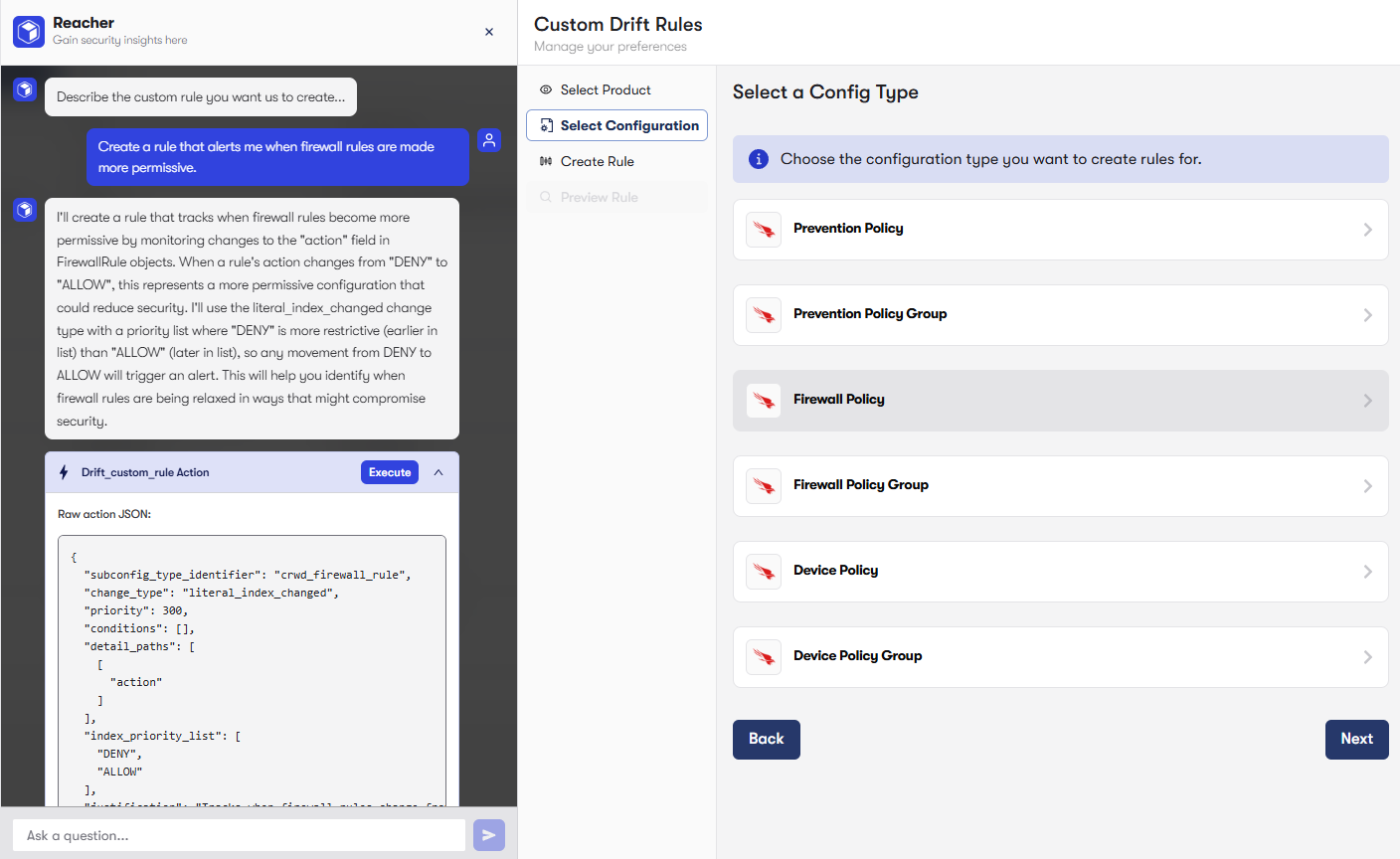
Conversational AI Support and Drift Rule Generation with Reacher™
Finally, Reach makes this intelligence accessible through Reacher™, our interactive AI agent. Need clarification about an exposure? Want your risk profile explained in plain language? Looking to generate a custom drift rule? Just ask. Reacher™ bridges the gap between technical detail and practical action, making security posture transparent and actionable.
Breaking the Spiral for Good
Cybersecurity doesn’t have to be an endless spiral of new tools, new alerts, and new workloads. By shifting focus left of boom—closing exposures before attackers exploit them—Reach gives security teams relief from the squeeze and empowers them to regain control of their defenses, get ahead of threats, maximize their existing security tool investments, and stop the cycle of reactive firefighting. To learn more about Reach, sign up for a demo.










