New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowReach continuously optimizes security tools, activating
high-value capabilities, remediating misconfigurations, and ensuring defenses operate at peak effectiveness against real-world threats.
Reach identifies and activates underused security capabilities across your stack based on your threat profile and priorities, maximizing the defensive value and ROI of the tools you already own.
Reach identifies underutilized and unused security capabilities across your stack and recommends which ones to activate based on your threat profile and risk priorities. Instead of leaving powerful controls dormant, Reach ensures your tools are deployed as their best versions. This dramatically increases the return on investment from existing security spend without adding new tools.

With thousands of configurations and hundreds of new features released annually, manual optimization simply does not scale. Reach’s domain-specific AI models continuously evaluate how tools are configured, how features interact, and where defensive strength can be improved. This allows organizations to optimize security posture at a speed, depth, and scale no human team can achieve.
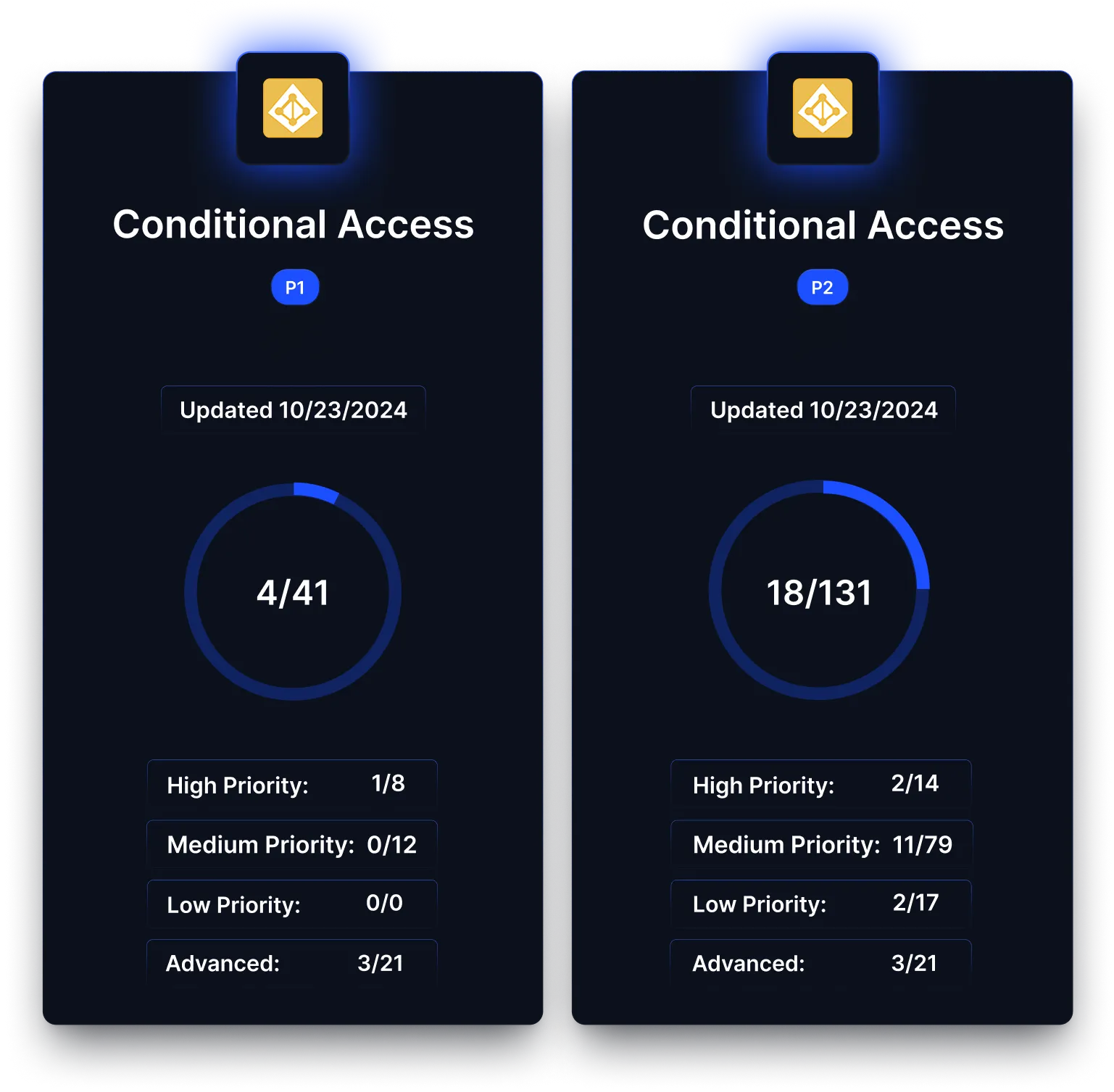
Optimization is not a one-off project. Reach continuously validates
configurations, detects drift, and re-optimizes controls as environments, threats, and vendor capabilities evolve. This ensures security tools remain tuned for maximum effectiveness over time, not just at the moment of deployment.

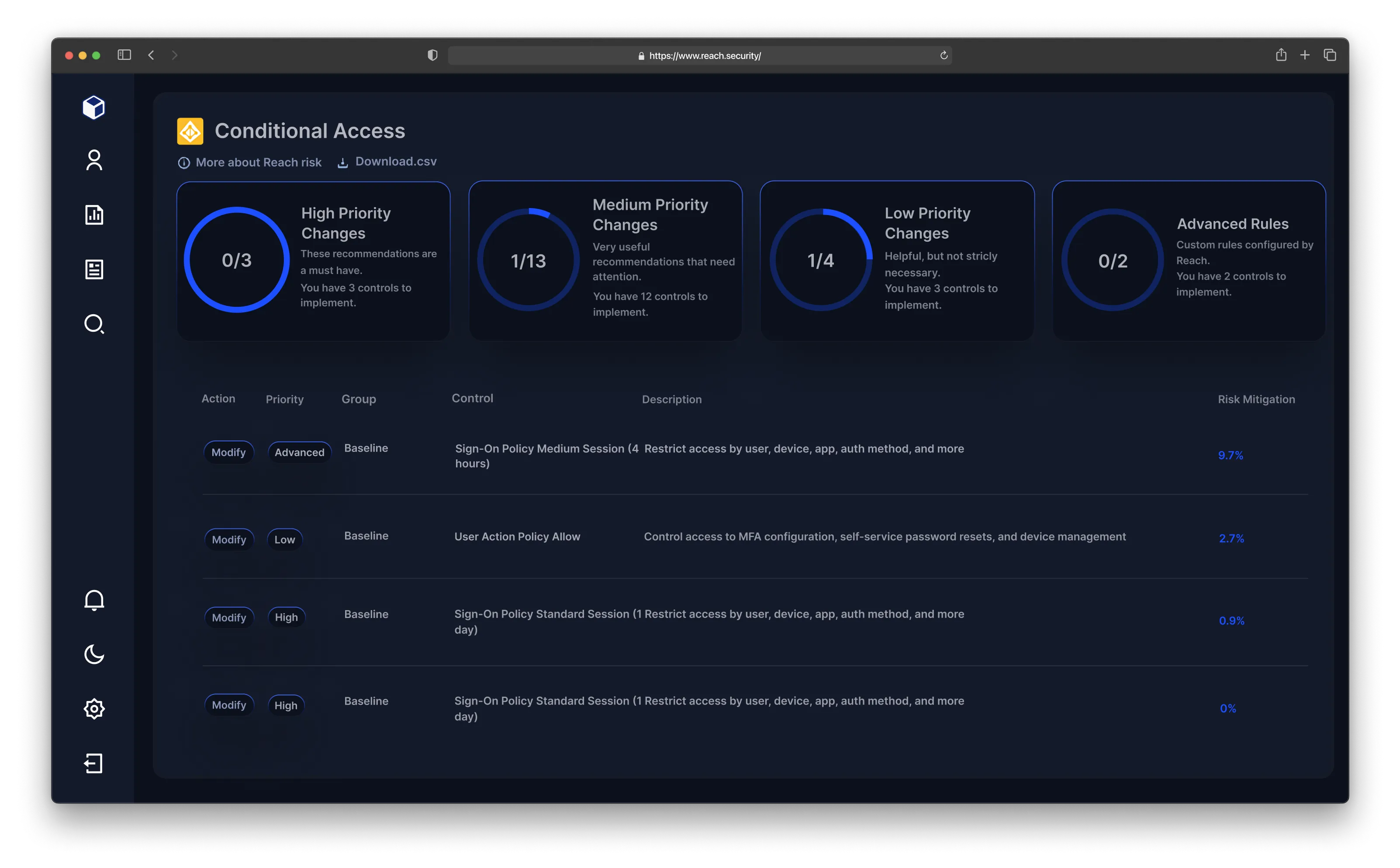
Reach identifies and prioritizes exposure risks across email, network, endpoint, SaaS applications, and identity access management. By focusing on the most relevant threats, Reach helps organizations safeguard their most vulnerable asset: their people.
Reach automates remediation with context-driven recommendations, deployment guides, and change tickets tailored to your tools and environment. This ensures security changes are actionable, reducing the time and effort required to improve your security posture.
By connecting to existing tools, Reach provides a clear view of risk exposure, prioritizes based on your unique threat profile, and offers actionable insights. This approach empowers security teams to focus on what matters most, avoiding wasted efforts.
Unlike platforms that stop at assessments, Reach bridges the gap by guiding action. With deep integrations, automated prioritization, and tailored remediations, Reach enables organizations to reduce exposure and better utilize their existing tools.
To join the community of customers enjoying the benefits of Reach and learn more about how it can transform your security posture, visit: