New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowReach provides continuous, centralized visibility into
security posture across identity, endpoint, email, SASE, and network controls, giving teams the insight and control needed to govern their defenses with confidence. This turns fragmented tooling into a coherent, measurable, and controllable security posture. The result: precise exposure mapping and a clear picture of organizational risk

Reduction in attack anatomy risk
Total number of attacks

People in this group
1.2% of your organization
Reach provides a single, consolidated view of configurations and controls across identity, endpoint, email, SASE, and network tools, revealing misconfigurations, weakened defenses, and drift that would otherwise remain hidden. Understand the effectiveness and state of your security tools at any given moment.
Reach connects directly to your existing security tools to provide a single, consolidated view of how defenses are configured across people, assets, and systems. Instead of relying on screenshots, assumptions, or tribal knowledge, security teams can clearly see which controls are enabled, misconfigured, weakened, or drifting over time. This creates a shared source of truth across security and IT teams.

Total number of Attacks
Number of Attacks Delivered
Numbers of Attacks Preventable
Reach transforms configuration data into measurable insights that
security teams can use to justify decisions and drive change. Whether validating that tools are aligned with policy or providing evidence to support configuration changes, Reach gives teams the analytical backing they need to move from intuition to proof. This enables proactive posture management rather than reactive firefighting.

Security posture is not static. Reach continuously monitors configurations to detect drift the moment it occurs and alerts teams when controls fall out of alignment with security objectives. This ensures visibility does not fade over time and that security maintains control even as environments, ownership, and tooling evolve.
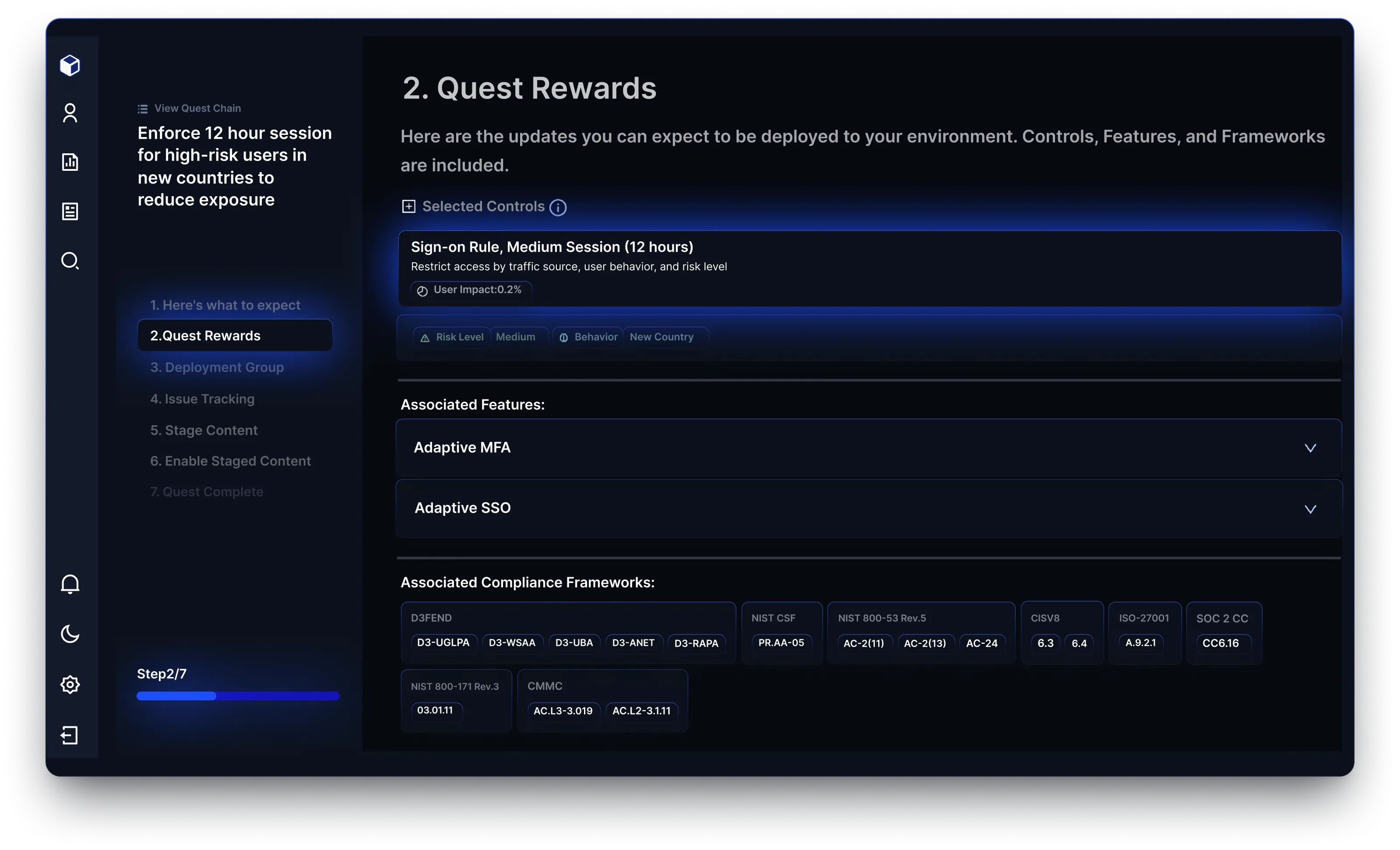
Reach identifies and prioritizes exposure risks across email, network, endpoint, SaaS applications, and identity access management. By focusing on the most relevant threats, Reach helps organizations safeguard their most vulnerable asset: their people.
Reach automates remediation with context-driven recommendations, deployment guides, and change tickets tailored to your tools and environment. This ensures security changes are actionable, reducing the time and effort required to improve your security posture.
By connecting to existing tools, Reach provides a clear view of risk exposure, prioritizes based on your unique threat profile, and offers actionable insights. This approach empowers security teams to focus on what matters most, avoiding wasted efforts.
Unlike platforms that stop at assessments, Reach bridges the gap by guiding action. With deep integrations, automated prioritization, and tailored remediations, Reach enables organizations to reduce exposure and better utilize their existing tools.
To join the community of customers enjoying the benefits of Reach and learn more about how it can transform your security posture, visit: