New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowReach leverages domain-specific AI models to understand
configurations and control deployments across your security stack, develop a genius-level understanding of how your tools are being used (and misused), and then intelligently modifies those configurations to harden defenses and supercharge security posture, at machine speed.

Reduction in attack anatomy risk
Total number of attacks

People in this group
1.2% of your organization
Reach’s purpose-built cybersecurity AI understands security tool configurations, control behavior, and attacker techniques, enabling precise identification of misconfigurations and underutilized defenses that generic AI and manual reviews miss.
Reach is powered by cybersecurity domain-specific AI models purpose-built to understand security controls, configurations, and attacker behavior across identity, endpoint, email, SASE, and network security tools. Unlike general- purpose AI, these models are trained on security telemetry, configuration schemas, threat intelligence, and frameworks, allowing them to reason accurately about real-world exposure. This deep specialization enables precise identification of misconfigurations and underutilized controls that manual reviews routinely miss.

Total number of Attacks
Number of Attacks Delivered
Numbers of Attacks Preventable
Modern security environments generate billions of data points across tools, configurations, and threat signals. Security toolsets are sprawling, amounting to thousands of configurations that need constant managing. Vendors ship hundreds of feature updates per year, making it unfeasible for teams to learn and deploy these capabilities fast and effectively. Hiring more personnel to manually address these problems will not scale.
Reach’s purpose-built AI engine automates configuration analysis and management, proactively learns about new feature releases across your stack and activates capabilities for maximum protection. This allows Reach to uncover hidden exposures, assess impact, and recommend action at a speed and magnitude that no human team alone – regardless of size – could replicate.

Reach does not stop at insight. Its AI prioritizes remediation based on exposure severity, attack behavior, and configuration context, then generates tool-specific, step-by-step remediation guidance aligned to frameworks like MITRE and Zero Trust. Reach validates changes in staged environments and executes remediation workflows across the security ecosystem, enabling organizations to close gaps continuously without adding operational burden. This elevates AI from an analytical assistant into an operational force multiplier for cybersecurity teams.
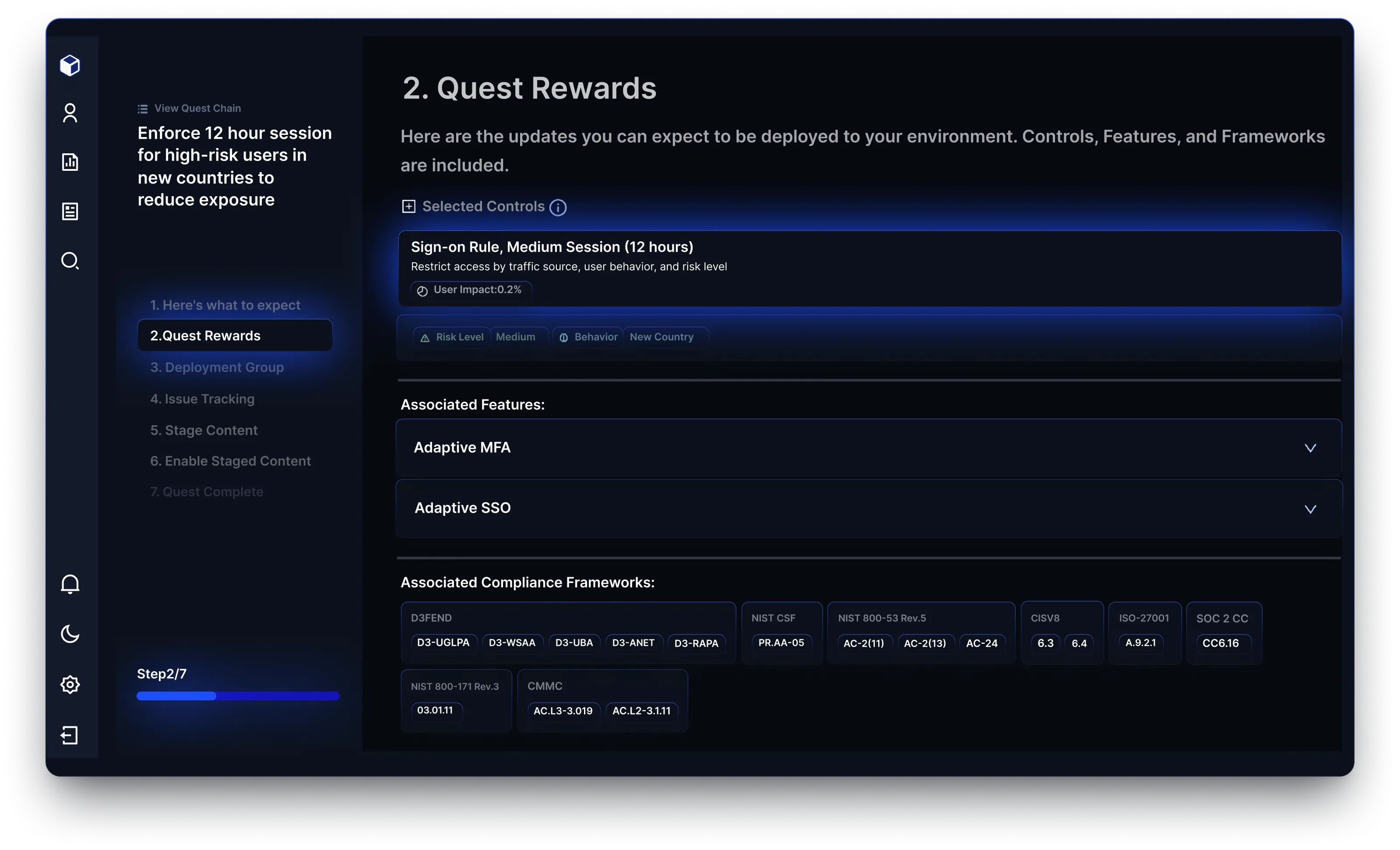
Reach identifies and prioritizes exposure risks across email, network, endpoint, SaaS applications, and identity access management. By focusing on the most relevant threats, Reach helps organizations safeguard their most vulnerable asset: their people.
Reach automates remediation with context-driven recommendations, deployment guides, and change tickets tailored to your tools and environment. This ensures security changes are actionable, reducing the time and effort required to improve your security posture.
By connecting to existing tools, Reach provides a clear view of risk exposure, prioritizes based on your unique threat profile, and offers actionable insights. This approach empowers security teams to focus on what matters most, avoiding wasted efforts.
Unlike platforms that stop at assessments, Reach bridges the gap by guiding action. With deep integrations, automated prioritization, and tailored remediations, Reach enables organizations to reduce exposure and better utilize their existing tools.
To join the community of customers enjoying the benefits of Reach and learn more about how it can transform your security posture, visit: