Refreshed and updated September 10th, 2025.
In cybersecurity, the "last mile" represents the crucial yet challenging phase where strategic plans translate into actionable security measures. This phase is critical, as it's where the effectiveness of security tools is truly tested. At Reach, we understand the importance of this last mile and are committed to helping our clients navigate it successfully. Building on our previous discussions on the maturity model and the last mile concept, we can now celebrate one full year since we integrated ServiceNow ITSM into Reach. It’s been a game changer.
Streamlining the Last Mile with ServiceNow
The ServiceNow integration marks a pivotal development in our effort to help our customers achieve Level 2 maturity. At this level, organizations go beyond merely generating reports and begin integrating actionable security measures directly into their operational workflows. By facilitating the creation of detailed, actionable tickets within users' workflow management systems, this integration significantly reduces the overhead associated with manual ticket handling. The integration ensures that each ticket is not only a notification of a task but a blueprint for action that aligns perfectly with the specific security needs of the organization.
Practical Benefits of our ServiceNow Integration
The integration with ServiceNow transforms the way security tasks are managed and executed. It automates the ticket creation process, populating tickets with all the necessary details required to address a security concern effectively. This means less time spent by teams writing up requirements and more time focusing on implementing solutions — a key factor in accelerating response times and enhancing the security posture of an organization.
This integration not only ensures that actionable tasks are seamlessly integrated into the daily workflows but also significantly enhances job satisfaction by reducing redundant, time-consuming work. It aligns with our goal of improving operational efficiency and job satisfaction, thereby aiding in better retention of skilled security professionals.
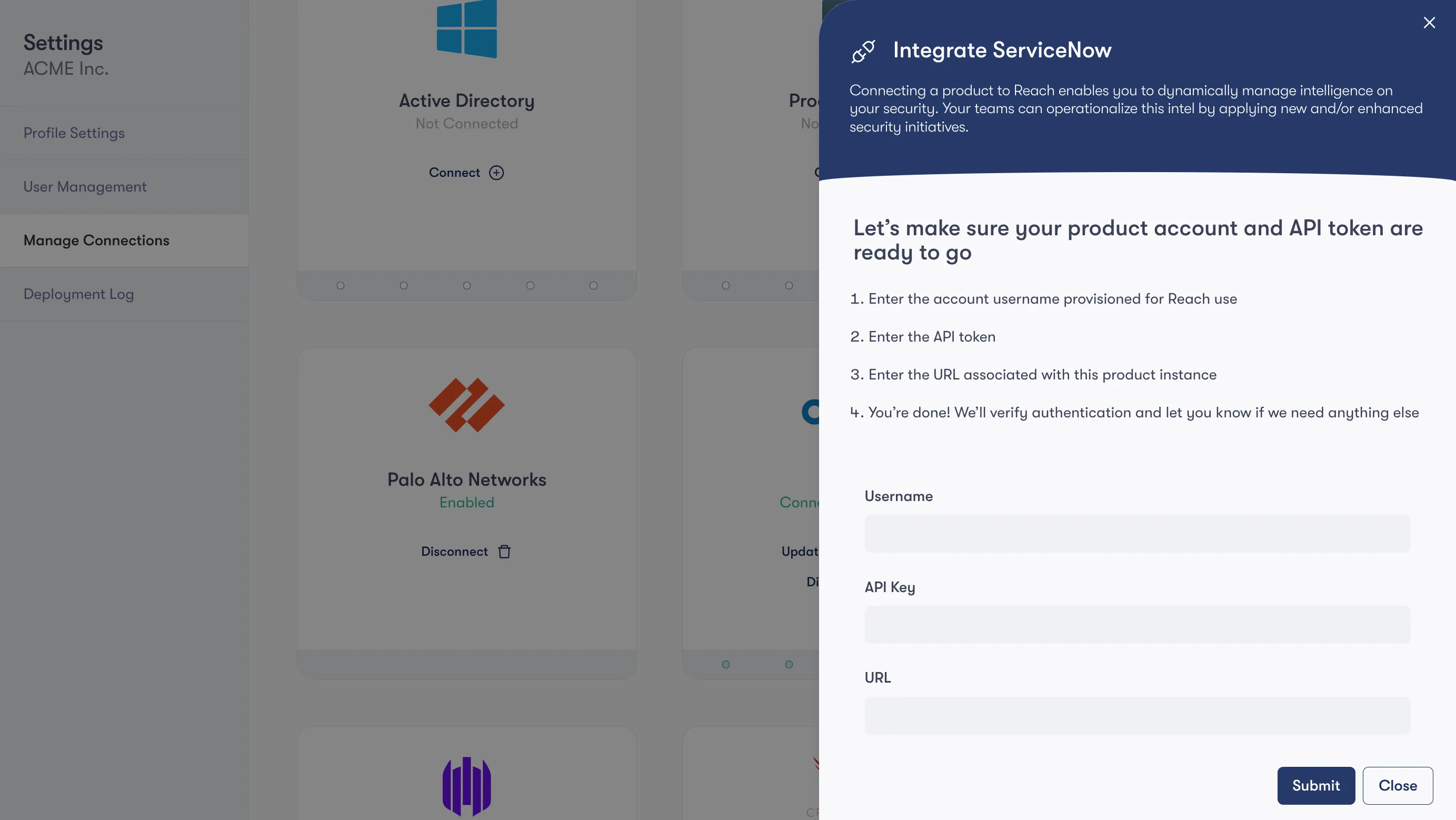
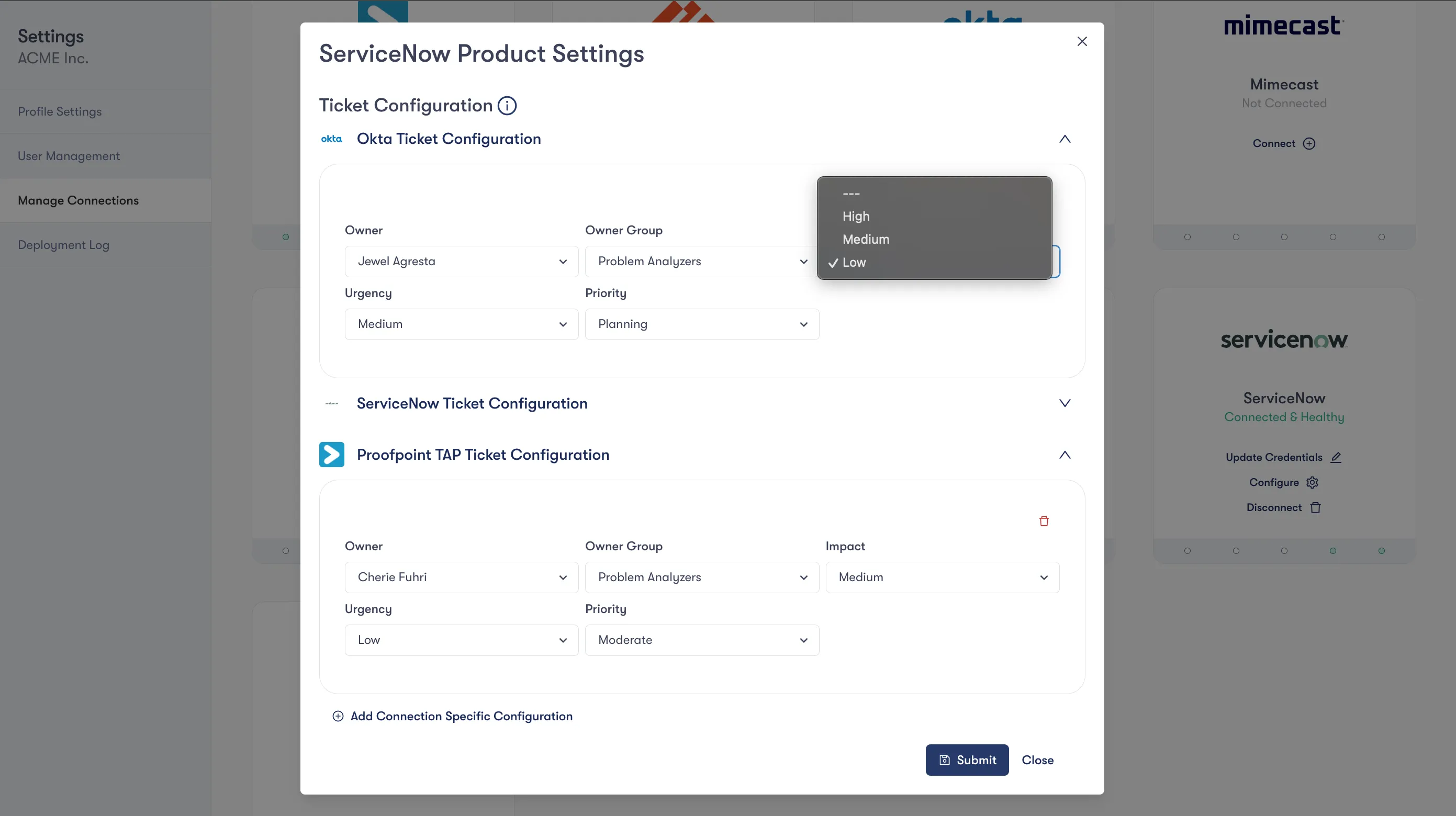
Our ServiceNow integration complements the existing integration with Jira, which we introduced as part of our commitment to addressing the last mile in cybersecurity. The Jira integration focuses on mapping changes to the correct project, issue type, and owner within an organization, ensuring that tasks are directed appropriately and managed efficiently. Together, these integrations provide a comprehensive solution that covers a broad spectrum of workflow management systems, catering to the diverse needs of our clients.
By situating the ServiceNow integration within the last mile concept and our cybersecurity maturity model, we emphasize our commitment to not just assessing risks but acting on them. As described in our maturity model, moving from Level 1 (Assessment) to Level 2 (Action) involves the transition from recognizing security gaps to actively implementing measures to address them. Our integrations with ServiceNow and Jira are critical in enabling organizations to make this transition effectively.
As we continue to navigate the complexities of cybersecurity, our focus remains on providing solutions that not only secure but also streamline operational processes. The ServiceNow integration is a testament to our dedication to mastering the last mile, ensuring that our clients can achieve and maintain the highest levels of security maturity.
More About Reach Security
Reach Security is the first platform that bridges the gap between knowing your exposure and actually fixing it. Security teams are overwhelmed by exposures from misconfigurations, vulnerabilities, and tool sprawl. Most solutions stop at reporting—Reach operationalizes remediation.
With Reach, organizations can:










