New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowA global leader in the manufacturing industry knew the benefits of utilizing SSL decryption on their Palo Alto Networks firewalls, but were cautious to implement the capability. It’s been a top priority for their IT Security Manager, an expert in PAN-OS, since joining the company. Since 80-90% of their network traffic was encrypted,extending visibility would allow his team to get a more complete picture of threats entering and exiting the network.
Concerns from the business around privacy and operational impact kept the project on hold for the better part of 6 years. Deploying this capability for all SSL traffic and to every employee in the workforce was not feasible. If he wanted buy in, the IT Security Manager knew he needed a data-driven, threat informed approach to rolling it out in phases, and to do so he needed to Identify who was being attacked the most in the organization and Identify where attackers were hiding their activities in encrypted web-traffic.
Within minutes, Reach connected to their security stack and Analyzed email forensics to quantify the number of threats and threat types utilizing encryption in their Delivery. Reach then Correlated these threats with workforce data to determine which users received these attacks, which were riskier than average, and which had a higher risk contribution relative to the rest of the workforce.
“I could write scripts to parse email forensics related to URLs used in attacks, or iterate through alerts tied to our workforce’s endpoints - but that is a manual, lengthy, and a resource-intensive process.”
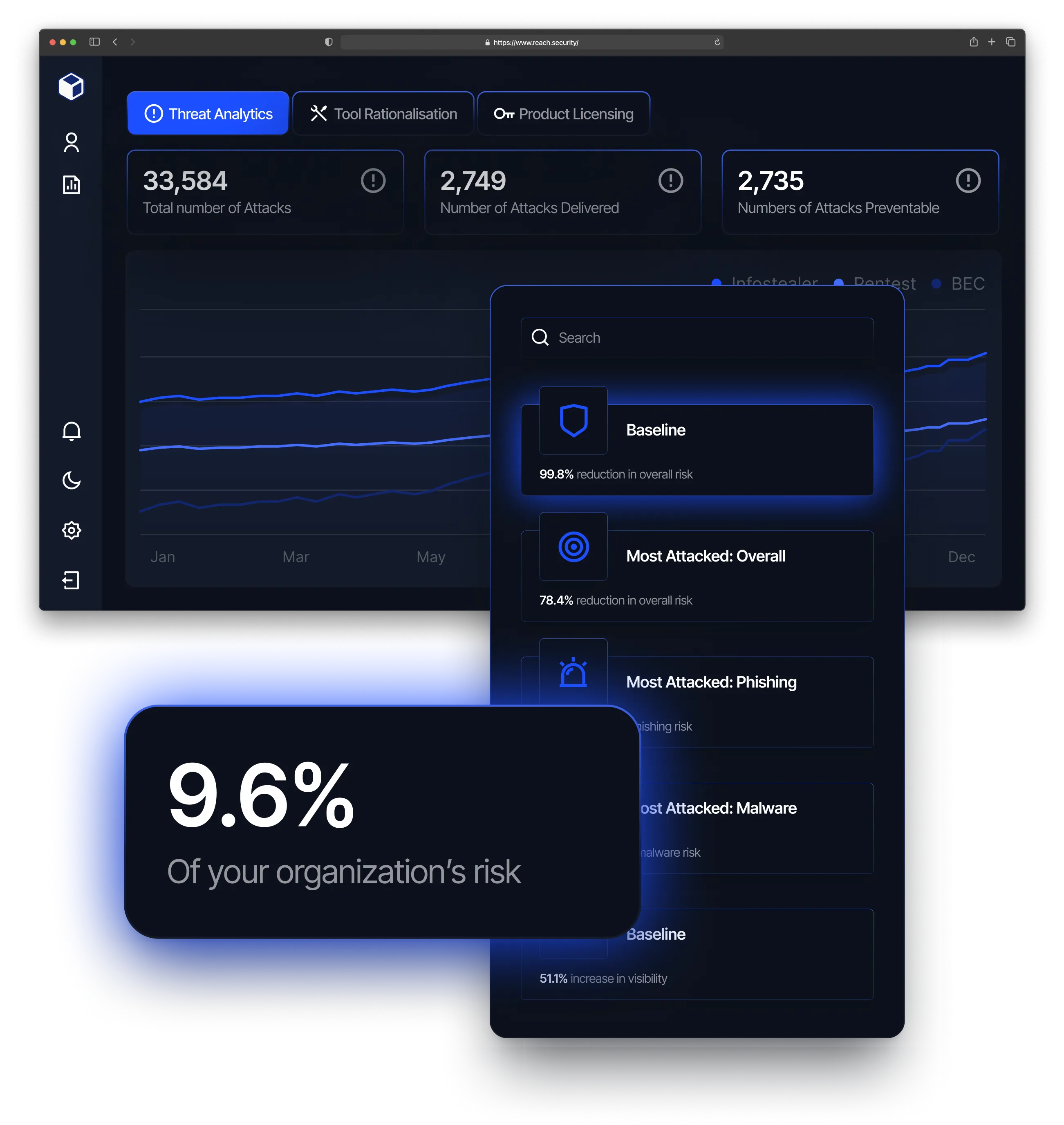
The result? A prioritized list of risky users derived from threat data and a realization that 4% of the population accounted for 70% of the company’s overall risk. Leadership now had data to understand that a majority of risk lived with a minority of users and gave the green light to start SSL decryption on a test group of those that were most attacked.
Balancing Security, Performance, and Business Needs

For Nutanix, Reach Security delivered exactly what was needed — enhanced protection, increased efficiency, and the confidence to scale securely. This partnership exemplifies the power of combining world-class infrastructure with intelligent, data-driven security solutions.
By combining seamless integration, proactive threat detection, automation, and adaptability, Reach Security delivers a comprehensive approach to cybersecurity that empowers organizations to stay ahead of the curve and confidently face an ever-changing threat landscape.
"Reach provides a single pane of glass for viewing your entire security ecosystem. Comprehensive dashboards and detailed reports enable you to understand your risk posture, track trends over time, and make informed decisions. These insights help refine your overall security strategy, ensuring that you stay ahead of emerging threats. Reach’s platform integrates smoothly with your existing infrastructure, ensuring minimal disruption during deployment. Our compatibility with a wide range of tools and environments allows you to quickly enhance your security posture without overhauling current processes."
"With Reach, I’m using terms like ‘these users provide more risk to the company overall’, and I’m actually able to give concrete numbers and something valuable to leadership.
9.6%

"With Reach, I'm now able to say 'I'm not decrypting all URL traffic, I'm decrypting these categories based on attacks that we've seen and reviewed. I'm decrypting these categories for our highest risk users. It's much more manageable."
Unlock the full power of your security stack with a free tool rationalization assessment.
Read-only API key for a security tool of your choice
Create your account and setup the integration
Get results across licensing, control mapping, risk exposure, and posture