New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowOperating in the heavily regulated insurance sector, Insurity needed to balance agility with strict security requirements. As both CIO and CISO, Jay Wilson leads an integrated IT and security team that must move fast while maintaining trust with customers. This dual mandate gave Jay visibility into how fragmented best-of-breed tools and evolving initiatives like Zero Trust placed operational burdens on his team.
Like many organizations, Insurity had started its Zero Trust journey, but implementation was complex. Early design decisions prioritized speed, allowing the team to move quickly, but Jay knew the architecture wasn’t yet fully aligned with Zero Trust principles. A project to analyze access patterns across their ZTNA provider had begun, but completing it required extensive manual work across fragmented systems.
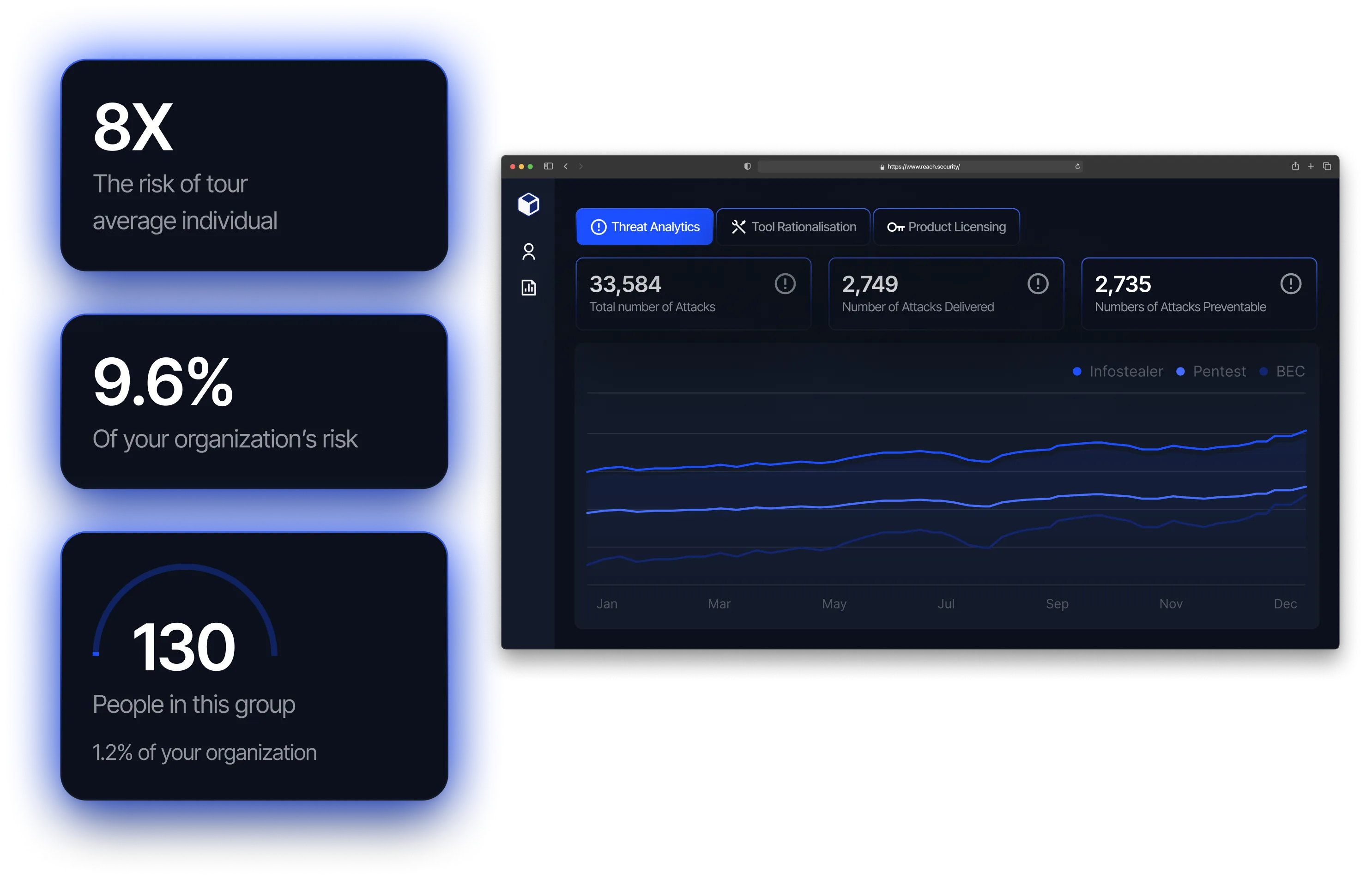
Insurity partnered with Reach to address these challenges and bring continuous posture management into their operations. Reach integrated with Insurity’s tech stack—including identity, network, endpoint, conditional access and email— to enable a unified and automated approach to optimizing security controls.
“Reach helps us manage new capabilities in ways we couldn’t before. It’s not just about starting a program, it’s about sustaining it efficiently over time.”
Since implementing Reach, Insurity has transformed its security operations and achieved several improvements:
Demand security talent has never been greater as the threat landscape continues to evolve.

Insurity began working with Reach to accelerate progress on critical security initiatives starting with Zero Trust, but with a roadmap that spans broader maturity improvements across the stack. One of the most impactful early use cases involved analyzing and optimizing access across the organization. Reach enabled Jay’s team to evaluate their implementation, surface risky patterns, and refine policies far faster than traditional methods allowed.
By combining seamless integration, proactive threat detection, automation, and adaptability, Reach Security delivers a comprehensive approach to cybersecurity that empowers organizations to stay ahead of the curve and confidently face an ever-changing threat landscape.
"Reach provides a single pane of glass for viewing your entire security ecosystem. Comprehensive dashboards and detailed reports enable you to understand your risk posture, track trends over time, and make informed decisions. These insights help refine your overall security strategy, ensuring that you stay ahead of emerging threats. Reach’s platform integrates smoothly with your existing infrastructure, ensuring minimal disruption during deployment. Our compatibility with a wide range of tools and environments allows you to quickly enhance your security posture without overhauling current processes"
“Reach helps us manage new capabilities in ways we couldn’t before. It’s not just about starting a program, it’s about sustaining it efficiently over time.”
9.6%

“Reach is in a unique position. They have the opportunity to create that ‘1 + 1 = 3’ moment across platforms and point tools. That’s the real power.”
Insurity views Reach as a long-term partner, not just a tool. As new tools and policies are introduced from access controls to endpoint and network configurations, Reach will play a role in enabling and maintaining them.
Unlock the full power of your security stack with a free tool rationalization assessment.
Read-only API key for a security tool of your choice
Create your account and setup the integration
Get results across licensing, control mapping, risk exposure, and posture