New Solution Guide: Find and Fix Ten Hidden Cybersecurity Misconfigurations in 2026
Download NowMonolithic Power Systems (MPS) is a leading provider of high-performance, semiconductor-based power solutions. With a reputation for innovation in data center communications and video acceleration, MPS supports thousands of global employees across 15 offices. Headquartered in Kirkland, WA, the company has seen rapid business expansion and increasing operational complexity.
When Huy Ly joined MPS, the company had just experienced a cyberattack. What started as an effort to stabilize a compromised environment quickly turned into a broader initiative to build a modern, resilient security program from the ground up. MPS partnered with Reach to enhance the security team’s visibility, efficiency, and control. Initially drawn to Reach’s Zero Trust and remediation-focused approach, Huy quickly realized the platform could help monitor and optimize tool configurations across email, EDR, and network security without adding more manual work.
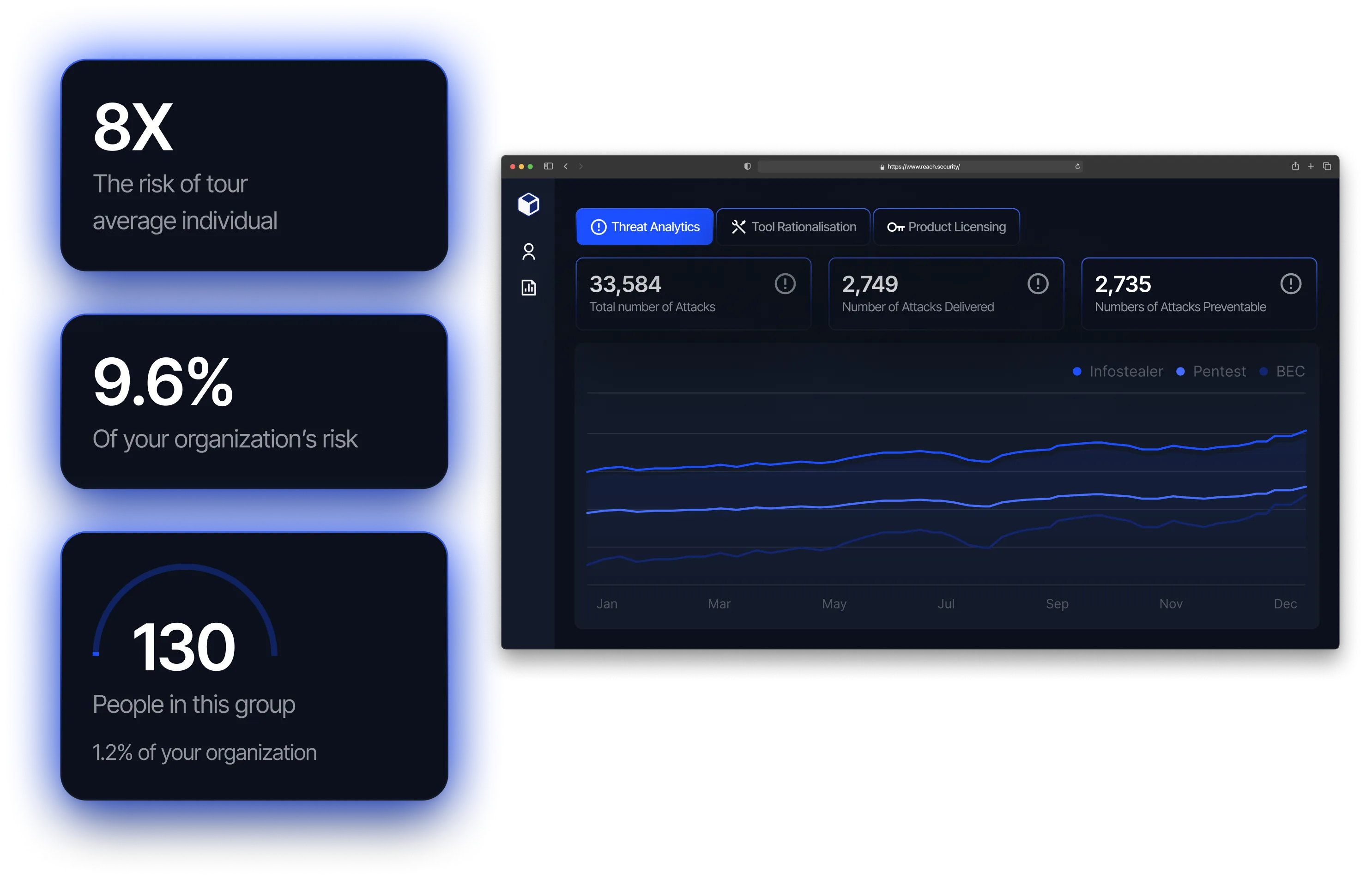
Monolithic Power Systems partnered with Reach to address these challenges and bring continuous posture management into their operations. Reach integrated with Monolithic Power Systems' tech stack—including identity, network, endpoint, conditional access and email— to enable a unified and automated approach to optimizing security controls.
“Reach became like a virtual assistant. It tells me what’s going on in the environment, what needs to change, and what’s getting missed.”
Since implementing Reach, Monolithic Power Systems has transformed its security operations and achieved several improvements:
Demand security talent has never been greater as the threat landscape continues to evolve.

Monolithic Power Systems began working with Reach to accelerate progress on critical security initiatives starting with Zero Trust, but with a roadmap that spans broader maturity improvements across the stack. One of the most impactful early use cases involved analyzing and optimizing access across the organization. Reach enabled Huy’s team to evaluate their implementation, surface risky patterns, and refine policies far faster than traditional methods allowed.
By combining seamless integration, proactive threat detection, automation, and adaptability, Reach Security delivers a comprehensive approach to cybersecurity that empowers organizations to stay ahead of the curve and confidently face an ever-changing threat landscape.
"Reach provides a single pane of glass for viewing your entire security ecosystem. Comprehensive dashboards and detailed reports enable you to understand your risk posture, track trends over time, and make informed decisions. These insights help refine your overall security strategy, ensuring that you stay ahead of emerging threats. Reach’s platform integrates smoothly with your existing infrastructure, ensuring minimal disruption during deployment. Our compatibility with a wide range of tools and environments allows you to quickly enhance your security posture without overhauling current processes"
“Security talent is limited. That’s why I partner with innovators; people willing to build with me. Reach fit that mindset perfectly.”
9.6%

“What keeps me up at night? The sophistication of attackers and how fast they move. With Reach, we’re not just keeping up, we’re getting ahead.”
Huy sees Reach as a strategic partner in evolving areas like AI, ransomware defense, and identity protection. With a strong foundation in place, the focus now turns to expanding coverage, closing gaps, and staying ahead of fast-moving threats.
Unlock the full power of your security stack with a free tool rationalization assessment.
Read-only API key for a security tool of your choice
Create your account and setup the integration
Get results across licensing, control mapping, risk exposure, and posture